Picture this: it’s 2 AM, your Kubernetes cluster is failing, and you’re staring at a Terraform configuration that looks like it was written by someone who hates your future self.
The deployment worked fine in staging, but production? Production is a different beast entirely.
If this sounds familiar, you’re not alone.
The dirty secret of Infrastructure as Code is that most teams are still winging it when it comes to security and code quality. Sure, we’ve automated the provisioning part, but we’re still manually reviewing infrastructure code like it’s 2015.
Recent data shows 73% of enterprises got hit with AI-related security incidents in the past year, costing an average of $4.8 million per breach.
Meanwhile, AI is now generating 25% of all new code according to Google. But the math isn’t creating infrastructure code faster than ever, but our review processes are stuck in the past.
The IaC market hit $850.6 million in 2024 and is growing at 24% annually, but the real story isn’t the growth, it’s the shift. Teams are finally realizing that “move fast and break things” doesn’t work when “things” are your production infrastructure.
This guide covers the 16 tools that actually matter in 2025, starting with the security and quality solutions that have become essential, then diving into the provisioning and configuration tools you need to know.
We're not sugarcoating anything, if a tool sucks, we'll tell you why.
Why Infrastructure Code Review is Broken (And What Actually Works)
Let’s talk about something nobody wants to admit: traditional infrastructure code review is fundamentally broken.
The typical process goes like this: Someone writes Terraform, submits a PR, and hopes their colleague catches the security issue where they accidentally opened port 22 to the internet.
Maybe they catch it.
Maybe they don’t.
Maybe they’re too busy to do a thorough review and just approve it because “it looks fine.”
This approach worked when teams were small and infrastructure changes were rare.
Now?
With teams pushing infrastructure changes daily and AI helping generate code, manual review doesn’t scale.
AI-Powered Code Review: The Tools That Actually Help
Manual reviews can’t keep up with daily infra changes and AI-generated code. That’s why teams are leaning on smarter, AI-powered tools that catch what humans miss. Here are the ones that actually help.
CodeAnt AI
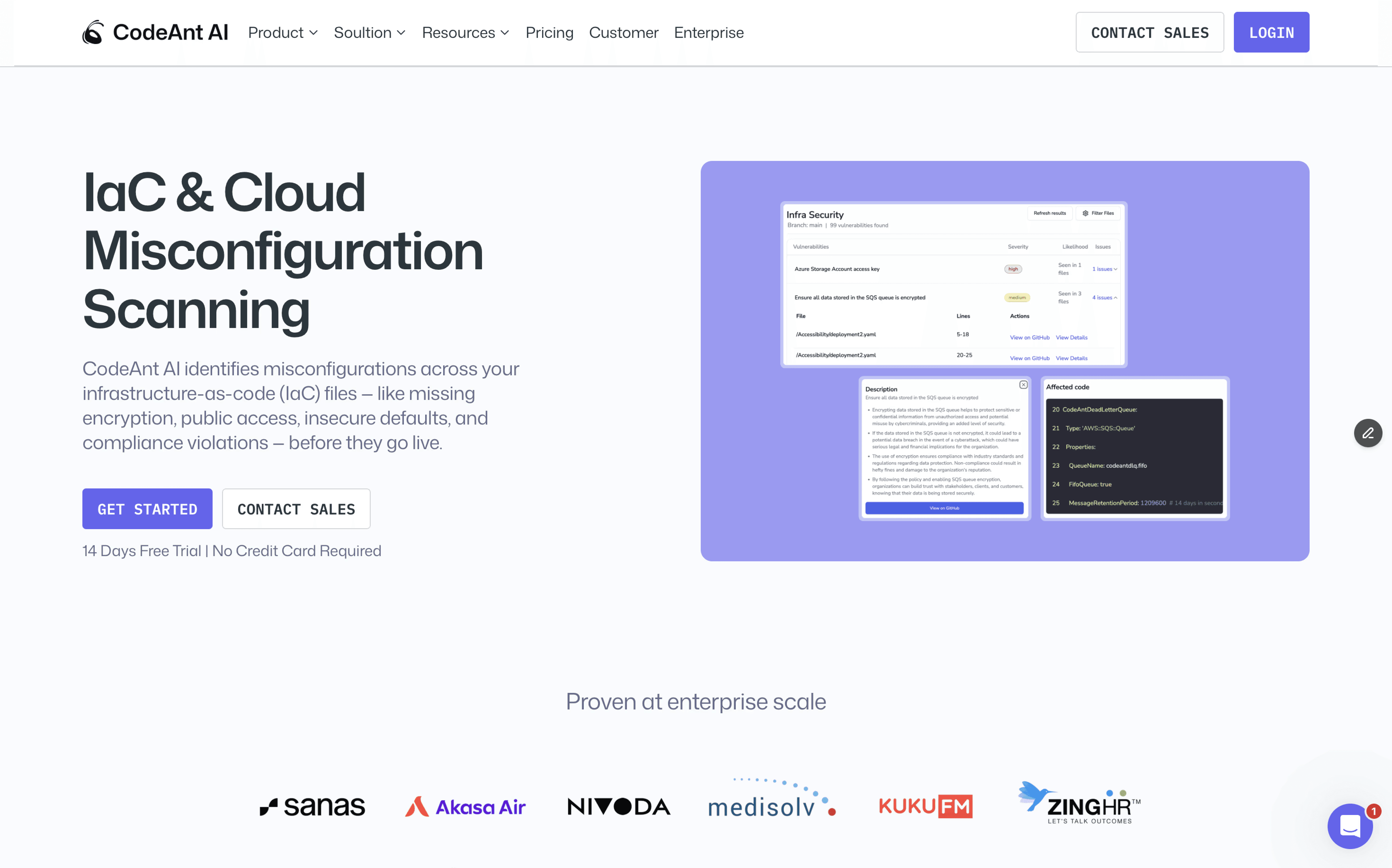
What it actually does
Intelligent infrastructure code review that doesn't suck
Why it matters
Because manual PR reviews miss critical security issues
Real talk
This is what code review should have been all along
Let me be blunt: if you’re not using AI to review code that AI helped write, you’re asking for trouble. CodeAnt AI solves the fundamental problem with infrastructure code review, context.
Traditional static scanners dump hundreds of warnings on your team and call it security. CodeAnt AI actually understands what your code is trying to do and explains why that S3 bucket configuration is a terrible idea before you push it to production.
We raised $2 million from Y Combinator in May 2025, but more importantly, teams like Fidelity and Motorq are using it to catch issues that would otherwise slip through manual review.
What makes it different
Reviews infrastructure code like a senior engineer would
Explains the actual impact of security issues, not just "this violates rule X"
Provides one-click fixes that actually work
Integrates with your existing Git workflow without slowing anyone down
The reality check
Works really well for common infrastructure patterns
Still learning edge cases and complex organizational policies
Requires some setup and team buy-in
Why teams are switching
Because catching a misconfiguration in PR review costs nothing. Catching it in production costs everything.
Getting started
14-day free trial with your existing Git setup. Their demo actually shows real security issues, not marketing fluff.
Pricing
Starts at $10/user/month (AI Code Review plan)
$15/user/month (Code Quality Platform)
$15/user/month (Code Security Platform)
14-day free trial available
Checkov

What it actually does
Finds the security issues you didn't know you had
Why it matters
Because "secure by default" is a myth
Real talk
Essential, but prepare for a lot of warnings initially
Checkov is like having a security auditor review every line of your infrastructure code. With 750+ built-in policies, it catches the mistakes that turn minor oversights into major incidents.
The first time you run Checkov on existing infrastructure code, you'll probably get overwhelmed by the number of issues it finds. Don't panic, most teams have hundreds of minor security issues they never knew about.
What it catches:
S3 buckets that are accidentally public
Security groups that are too permissive
Unencrypted databases and storage
Missing backup configurations
Compliance violations across major frameworks
The learning curve:
Easy to install and run
Takes time to tune policies for your environment
Can generate false positives without proper configuration
Works best when integrated into CI/CD from the start
Why it's essential
Because the security issue you don't know about is the one that will bite you.
Getting started
pip install checkov and run it on your existing code. Prepare to learn things you didn't want to know about your infrastructure.
Pricing
Free (Open source under Apache 2.0 license)
Spacelift

What it actually does
Makes multi-tool IaC management less painful
Why it matters
Because most teams use more than one IaC tool
Real talk
Enterprise-grade orchestration that actually works
Here's something nobody talks about: managing multiple IaC tools across teams is harder than the tools themselves.
Spacelift brings sanity to environments where some teams use Terraform, others use Pulumi, and everyone’s trying to coordinate deployments.
Half of Spacelift’s deployments are now running OpenTofu, which tells you something about where the market is heading.
What it solves:
Coordinating deployments across multiple IaC tools
Policy enforcement that actually gets followed
Drift detection that doesn't generate noise
Approval workflows that don't slow teams down
When you need it:
Multiple teams with different IaC preferences
Complex environments with dependencies between stacks
Enterprise governance and compliance requirements
More than a handful of people managing infrastructure
The trade-offs:
Commercial platform with real costs
Learning curve for workflow configuration
Probably overkill for small teams
Worth it when coordination becomes a problem
Getting started
Free tier lets you test with real workloads. Their onboarding actually explains how to organize complex environments.
Pricing
Free tier available, Starter plan at $250/month, Starter+ and Business plans (annual), Enterprise (custom pricing)
Infrastructure Provisioning: The Tools That Build Things
Once your reviews are solid, you still need reliable ways to actually spin up infrastructure. These provisioning tools are what turn code into running systems.
OpenTofu

What it actually does
Terraform without the vendor lock-in anxiety
Why it matters
Because depending on one company for critical infrastructure is risky
Real talk
This is where smart teams are heading
Remember when HashiCorp changed Terraform’s license and everyone freaked out? The community didn’t just complain, they built something better.
OpenTofu isn’t just a Terraform fork; it’s proof that community-driven development can outpace corporate priorities. Fidelity recently announced they’re switching to OpenTofu as their default IaC platform. When a financial giant publicly ditches Terraform, that’s not news, that’s a signal.
Why teams are switching:
Same syntax and providers as Terraform, but actually open source
Features Terraform users requested for years (like state encryption)
Linux Foundation governance means no surprise license changes
Growing faster than anyone expected
What you get:
Drop-in replacement for Terraform
Built-in state encryption (finally!)
Early variable evaluation that actually works
Dynamic providers for complex scenarios
The honest assessment:
Newer project with smaller ecosystem (but growing fast)
Some tooling still catching up to Terraform support
Feature development sometimes lags HashiCorp's resources
Worth the switch for long-term peace of mind
Migration reality:
If you're using Terraform 1.6 or earlier, migration is straightforward. Their docs include step-by-step guides that actually work.
Getting started
Start with a non-critical project and migrate gradually. Most teams are surprised how smooth the transition is.
Pricing
Free (Open source under Mozilla Public License 2.0)
5. Terraform

What it actually does
The infrastructure tool everyone knows
Why it still matters
Massive ecosystem and proven track record
Real talk
Still good, but the license situation is awkward
Terraform is the 800-pound gorilla of IaC. It’s battle-tested, well-documented, and has solutions for pretty much every infrastructure problem you can imagine. The Business Source License situation creates some uncertainty, but it's not going anywhere soon.
Why it's still relevant:
Largest ecosystem with 3,900+ providers
Proven at massive scale (Netflix, Uber, etc.)
Most comprehensive third-party tooling
Best documentation and learning resources
The license reality:
BSL allows most common use cases
Creates uncertainty for some commercial scenarios
Risk of future restrictions or changes
Some teams switching to OpenTofu as insurance
When to stick with Terraform:
Heavily invested in HashiCorp ecosystem
Using enterprise features not available elsewhere
Need maximum provider and tooling compatibility
Comfortable with license terms
The honest take:
Still a solid choice if the license terms work for your organization. Just have an exit strategy
Getting started
HashiCorp Learn platform has excellent free tutorials.
Pricing
Free (Community edition), Terraform Cloud has free tier, Standard and Plus plans (RUM-based pricing) varies.
6. Pulumi

What it actually does
Infrastructure code using real programming languages
Why developers love it:
Because DSLs are annoying
Real talk:
Game-changer for teams that think in code
While everyone else argues about YAML vs HCL, Pulumi lets you use actual programming languages. Python, TypeScript, Go, C#, if you can code in it, you can manage infrastructure with it. This isn’t just convenience. Real programming languages mean real programming constructs: loops, conditionals, functions, classes, and all the abstractions that make complex systems manageable.
Why it's different:
Use languages your team already knows
Actual programming constructs (loops, functions, classes)
Superior testing and debugging capabilities
Native package manager integration
Who should use it:
Developer-heavy teams tired of learning DSLs
Complex infrastructure requiring dynamic logic
Teams that want to test infrastructure code properly
Organizations standardizing on specific languages
The trade-offs:
Learning curve for traditional ops teams
Smaller ecosystem than Terraform/OpenTofu
Risk of over-engineering infrastructure
Can be overkill for simple deployments
Getting started:
Pick your favorite language and follow their guides. The Python tutorial is particularly good for infrastructure beginners.
Pricing
Free for individuals, Team edition at $0.0005 per Pulumi Credit (resource-hour), Enterprise starts at ~$32,850/year, Business Critical starts at ~$50,000/year
7. AWS CloudFormation

What it actually does
AWS infrastructure the Amazon way. Deepest AWS integration possible
Real talk
Perfect for AWS-only shops, painful for everyone else
If you're all-in on AWS and plan to stay that way, CloudFormation gives you the deepest possible integration. New AWS services often show up in CloudFormation before the APIs are fully documented.
The AWS advantage:
Immediate support for new AWS services
No external state management headaches
Direct AWS support when things break
Best integration with AWS governance tools
The reality check:
AWS-only means no multi-cloud flexibility
YAML/JSON syntax gets ugly fast
Limited reusability compared to modern tools
Can't use the same skills elsewhere
When it makes sense:
Committed to AWS long-term
Need immediate access to new AWS features
Want direct AWS support for infrastructure issues
Prefer vendor-managed solutions
Getting started:
AWS documentation is comprehensive. The CloudFormation Designer helps visualize complex templates.
Pricing
Free (AWS service - you only pay for the AWS resources created)
8. Azure Bicep

What it actually does
ARM templates that don't make you cry
Why it exists
Because nobody likes JSON hell
Real talk
What ARM templates should have been from the start
Microsoft looked at ARM templates, saw the mess they created, and built Bicep to fix it. Same functionality, readable syntax, and tooling that doesn't fight you.
Why it's better than ARM:
Human-readable syntax instead of JSON nightmare
Strong typing prevents stupid mistakes
Excellent VS Code integration
Compiles to ARM so it's not a separate platform
The limitations:
Still Azure-only
Smaller community than multi-cloud tools
Limited third-party tooling
Need to learn Microsoft's way of thinking
When to choose it:
Azure-focused organization
Migrating from ARM templates
Want modern tooling for Azure infrastructure
Prefer Microsoft's ecosystem
Getting started:
Microsoft Learn modules are actually good. The playground environments let you experiment safely.
Pricing
Free (Open source, compiles to ARM templates)
Configuration Management: Making Servers Do What You Want
Provisioning gets your infra up, but someone still has to keep those servers in line. That’s where configuration management comes in, tools built to make servers actually do what you want, consistently
9. Ansible

What it actually does
Configuration management that doesn't require a PhD
Why it's popular
No agents, readable YAML, just works
Real talk
The Swiss Army knife of automation
Ansible is what happens when someone builds automation tools for normal humans. No agents to manage, readable playbooks, and it works on pretty much everything.
Why teams love it:
No software to install on target systems
YAML that humans can actually read
Works for both config management and infrastructure provisioning
Huge library of pre-built modules
Where it struggles:
Performance isn't great for large deployments
State management is messy compared to other tools
Can get complex with dependencies
Not ideal for infrastructure-heavy workloads
Best use cases:
Hybrid environments with diverse systems
Teams that need both config and infrastructure automation
Organizations that want simple, understandable automation
Environments where agents aren't practical
Getting started:
Community documentation is excellent. Red Hat's training materials are worth the investment.
Pricing
Free (Open source under GPL license)
10. Chef

What it actually does:
Enterprise-grade configuration management
Why enterprises use it:
Compliance and policy enforcement that actually works
Real talk:
Powerful but complex
Chef is the tool you use when configuration management is serious business. It’s Ruby-based, test-driven, and designed for environments where compliance isn’t optional.
Enterprise strengths:
Robust testing framework for infrastructure
Comprehensive compliance and audit capabilities
Detailed reporting and audit capabilities
Mature ecosystem for complex environments
The complexity cost:
Steep learning curve requiring Ruby skills
Complex architecture with multiple moving parts
Higher overhead than simpler alternatives
Can be overkill for straightforward needs
When it makes sense:
Large, complex environments
Strict compliance requirements
Teams with Ruby expertise
Organizations that need comprehensive reporting
Getting started:
Progress Chef's training programs are comprehensive. Community cookbooks provide good starting points.
Pricing
Free tier available, Commercial plans start around $189/node/year (contact for enterprise pricing)
11. Puppet

What it actually does:
Keeps thousands of systems in line
Why it's still relevant:
State management at scale
Real talk:
Old but reliable
Puppet has been around forever in infrastructure terms, but it’s still relevant because it solves state management really well across large environments.
What it does well:
Manages desired state across thousands of systems
Automatic dependency resolution
Comprehensive reporting on system state
Mature ecosystem with extensive modules
The operational reality:
Complex setup and ongoing maintenance
Resource-intensive master/agent architecture
Learning curve for Puppet's DSL
Can be overwhelming for smaller environments
Best fit scenarios:
Large environments requiring state consistency
Teams with existing Puppet expertise
Organizations needing detailed compliance reporting
Environments where centralized control is important
Getting started:
Puppet Education provides structured paths. Puppet Forge has modules for common scenarios.
Pricing
Free (Open source version), Enterprise pricing varies (contact for quote)
Kubernetes and Cloud-Native Tools
For teams living and breathing Kubernetes, the next step is managing infrastructure the same way you manage pods and services. These cloud-native tools extend Kubernetes into a universal control plane.
12. Crossplane

What it actually does:
Kubernetes-native infrastructure management
Why it matters:
Everything-through-Kubernetes approach
Real talk:
Complex but powerful for Kubernetes-centric orgs
If your world revolves around Kubernetes, Crossplane turns your cluster into a universal control plane for infrastructure. It’s not simple, but it unifies how you manage everything.
The Kubernetes advantage:
Manage infrastructure using familiar Kubernetes patterns
Strong GitOps integration
Unified APIs across cloud providers
Perfect for platform engineering approaches
The complexity trade-off:
Requires deep Kubernetes knowledge
Complex setup and operations
Limited value outside Kubernetes environments
Steep learning curve for traditional infrastructure teams
When it makes sense:
Kubernetes-centric organization
Platform engineering initiatives
Teams already deep in cloud-native patterns
Need for unified infrastructure APIs
Getting started:
CNCF docs are comprehensive. Start with simple examples before attempting complex compositions.
Pricing
Free (Open source under Apache 2.0 license)
13. AWS CDK

What it actually does
AWS infrastructure using real programming languages
Why developers like it
Familiar syntax, deep AWS integration
Real talk
Great for AWS, vendor lock-in for everything else
AWS CDK lets you define infrastructure using the same languages you use for applications. It's not just convenience, it's a fundamentally different approach to infrastructure definition.
Developer benefits:
Use languages your team already knows
Excellent IDE support and debugging
Strong typing prevents configuration errors
Natural patterns for complex logic
The AWS reality:
Deep integration with AWS services
Vendor lock-in by design
Can't easily migrate to other clouds
AWS-specific patterns and constructs
Best scenarios:
AWS-committed organizations
Developer-heavy teams
Complex infrastructure requiring programming logic
Teams wanting modern development patterns
Getting started
AWS workshops are well-designed. Language-specific guides provide good starting points.
Pricing
Free (AWS service – you only pay for the underlying AWS resources)
Security and Specialized Tools
Even with the best provisioning and config tools, none of it matters if your stack isn’t secure. These security and specialized tools help you catch the vulnerabilities hiding in plain sight.
14. Trivy

What it actually does:
Finds vulnerabilities in everything
Why security teams like it:
Comprehensive scanning that actually works
Real talk:
Essential for container and infrastructure security
Trivy scans containers, filesystems, Git repositories, and infrastructure code for vulnerabilities and misconfigurations. It's fast, accurate, and finds things that matter.
Comprehensive coverage:
Container image vulnerabilities
Infrastructure code misconfigurations
Filesystem and dependency scanning
Secret detection in code repositories
Why it's practical:
Fast scanning with minimal false positives
Easy CI/CD integration
Constantly updated vulnerability database
Works well in automated workflows
Integration reality:
Simple to set up and use
Can generate noise without proper filtering
Requires workflow integration for maximum value
Works best as part of comprehensive security strategy
Getting started:
Installation is simple. CI/CD examples help with workflow integration.
Pricing
Free (Open source under Apache 2.0 license)
15. env0

What it actually does:
IaC automation with cost focus
Why finance teams like it:
Actual cost visibility and control
Real talk:
Good for teams serious about cloud spend
env0 provides automation and governance for multiple IaC tools, with strong emphasis on cost optimization and financial operations.
Cost management strengths:
Detailed cost estimation before deployment
Policy enforcement around spending
Multi-cloud cost optimization
Integration with FinOps workflows
Platform capabilities:
Support for multiple IaC tools
Workflow automation and governance
Policy enforcement and compliance
Cost tracking and optimization
Commercial considerations:
Pricing reflects enterprise focus
Learning curve for policy configuration
May be overkill for cost-insensitive environments
Best value for teams with complex cost requirements
Getting started:
Free tier provides good evaluation capabilities. Cost optimization guides are practical.
Pricing
Free tier available, paid plans start around $399/month (contact for enterprise pricing)
16. DNSControl

What it actually does:
DNS management that doesn't suck
Why it matters:
Because DNS outages take down everything
Real talk:
Simple tool that solves a specific problem well
DNS management through web interfaces is terrible. DNSControl treats DNS like code, with version control, testing, and automation for critical infrastructure.
Why it's essential:
Version control for DNS changes
Testing and validation before deployment
Multi-provider management from single source
Automation for complex DNS scenarios
Simplicity advantage:
Focused on DNS, does it well
Clear syntax for DNS records
Good provider support
Straightforward to learn and use
Scope limitations:
Only handles DNS use cases
Smaller community than general tools
Requires DNS knowledge for complex setups
Limited to DNS automation scenarios
Getting started:
Documentation includes practical examples. Migration guides help move from existing DNS setups.
Pricing
Free (Open source under MIT License)
Building an IaC Strategy That Actually Works
The tools matter, but strategy matters more. Here's how to build infrastructure automation that doesn't create more problems than it solves:
Start with the Pain Points
Fix Code Review First Most teams are still reviewing infrastructure code manually. Tools like CodeAnt AI solve the fundamental scalability problem with infrastructure review. Start here before optimizing other parts of the workflow.
Address Security Early Security scanning with tools like Checkov should be part of your workflow from day one, not bolted on later. The cost of implementing security review early is nothing compared to cleaning up after a breach.
Plan for Complexity Most organizations end up with multiple IaC tools. Tools like Spacelift become essential once you have more than one team or more than one tool in production.
Match Tools to Reality
Team Skills Trump Features Choose tools your team can actually use effectively. Pulumi makes sense for development teams. OpenTofu/Terraform work for mixed teams. Ansible fits operations-focused environments.
Cloud Strategy Determines Tools Single cloud? Use native tools for deepest integration. Multi-cloud? Stick with community standards like OpenTofu. Kubernetes-focused? Consider cloud-native approaches like Crossplane.
Size Affects Everything Small teams need tools that just work. Large organizations need governance, policy enforcement, and coordination capabilities. Don't over-engineer for scale you don't have.
Avoid Common Mistakes
Don't Try to Standardize Everything Different teams have different needs. Forcing everyone onto the same tool often creates more problems than it solves.
Security Isn't Optional 73% of enterprises had AI-related security incidents last year. Security review and scanning need to be built into workflows, not added later.
Plan for Change The Terraform licensing situation showed that depending on a single vendor for critical tools is risky. Choose tools and strategies that give you options.
The Real Talk Summary
Infrastructure as Code in 2025 isn't about choosing the "best" tool, it's about building workflows that scale with your team and protect against the risks that come with rapid, AI-assisted development.
What's actually changed in 2025:
AI-powered code review has become essential, not optional
OpenTofu's momentum is real, 20% of new projects start there
Security scanning needs to be built into workflows from the start
Multi-tool orchestration platforms solve real coordination problems
What hasn't changed:
Team skills matter more than tool features
Simple solutions beat complex ones for most use cases
Security bolted on later doesn't work
Tool choices should align with cloud strategy
The bottom line: Start with tools that solve your biggest pain points first. For most teams in 2025, that means intelligent code review, comprehensive security scanning, and infrastructure provisioning that doesn't lock you into a single vendor's roadmap.
The Bottom Line: Choose Tools That Actually Work Together
After diving into 16 different IaC tools, here's what matters most: your infrastructure is only as secure as your weakest review process. You can have the best provisioning tools in the world, but if you're missing critical security issues during code review, you're setting yourself up for expensive problems later.
The smart teams we see aren't just picking one perfect tool—they're building workflows where security, provisioning, and configuration management actually work together. They're using AI to catch what manual reviews miss, choosing open-source tools like OpenTofu for long-term flexibility, and implementing comprehensive scanning before anything hits production.
Start with what's broken first. For most teams, that's the one that never happens.
Ready to see what intelligent infrastructure code review looks like? Try CodeAnt AI free for 14 days and watch it catch the security issues your team would otherwise miss. No setup headaches, no credit card required, just connect your repo and see the difference AI-powered review makes.
Because the best infrastructure security incident is the one that never happens.
Picture this: it’s 2 AM, your Kubernetes cluster is failing, and you’re staring at a Terraform configuration that looks like it was written by someone who hates your future self.
The deployment worked fine in staging, but production? Production is a different beast entirely.
If this sounds familiar, you’re not alone.
The dirty secret of Infrastructure as Code is that most teams are still winging it when it comes to security and code quality. Sure, we’ve automated the provisioning part, but we’re still manually reviewing infrastructure code like it’s 2015.
Recent data shows 73% of enterprises got hit with AI-related security incidents in the past year, costing an average of $4.8 million per breach.
Meanwhile, AI is now generating 25% of all new code according to Google. But the math isn’t creating infrastructure code faster than ever, but our review processes are stuck in the past.
The IaC market hit $850.6 million in 2024 and is growing at 24% annually, but the real story isn’t the growth, it’s the shift. Teams are finally realizing that “move fast and break things” doesn’t work when “things” are your production infrastructure.
This guide covers the 16 tools that actually matter in 2025, starting with the security and quality solutions that have become essential, then diving into the provisioning and configuration tools you need to know.
We're not sugarcoating anything, if a tool sucks, we'll tell you why.
Why Infrastructure Code Review is Broken (And What Actually Works)
Let’s talk about something nobody wants to admit: traditional infrastructure code review is fundamentally broken.
The typical process goes like this: Someone writes Terraform, submits a PR, and hopes their colleague catches the security issue where they accidentally opened port 22 to the internet.
Maybe they catch it.
Maybe they don’t.
Maybe they’re too busy to do a thorough review and just approve it because “it looks fine.”
This approach worked when teams were small and infrastructure changes were rare.
Now?
With teams pushing infrastructure changes daily and AI helping generate code, manual review doesn’t scale.
AI-Powered Code Review: The Tools That Actually Help
Manual reviews can’t keep up with daily infra changes and AI-generated code. That’s why teams are leaning on smarter, AI-powered tools that catch what humans miss. Here are the ones that actually help.
CodeAnt AI

What it actually does
Intelligent infrastructure code review that doesn't suck
Why it matters
Because manual PR reviews miss critical security issues
Real talk
This is what code review should have been all along
Let me be blunt: if you’re not using AI to review code that AI helped write, you’re asking for trouble. CodeAnt AI solves the fundamental problem with infrastructure code review, context.
Traditional static scanners dump hundreds of warnings on your team and call it security. CodeAnt AI actually understands what your code is trying to do and explains why that S3 bucket configuration is a terrible idea before you push it to production.
We raised $2 million from Y Combinator in May 2025, but more importantly, teams like Fidelity and Motorq are using it to catch issues that would otherwise slip through manual review.
What makes it different
Reviews infrastructure code like a senior engineer would
Explains the actual impact of security issues, not just "this violates rule X"
Provides one-click fixes that actually work
Integrates with your existing Git workflow without slowing anyone down
The reality check
Works really well for common infrastructure patterns
Still learning edge cases and complex organizational policies
Requires some setup and team buy-in
Why teams are switching
Because catching a misconfiguration in PR review costs nothing. Catching it in production costs everything.
Getting started
14-day free trial with your existing Git setup. Their demo actually shows real security issues, not marketing fluff.
Pricing
Starts at $10/user/month (AI Code Review plan)
$15/user/month (Code Quality Platform)
$15/user/month (Code Security Platform)
14-day free trial available
Checkov

What it actually does
Finds the security issues you didn't know you had
Why it matters
Because "secure by default" is a myth
Real talk
Essential, but prepare for a lot of warnings initially
Checkov is like having a security auditor review every line of your infrastructure code. With 750+ built-in policies, it catches the mistakes that turn minor oversights into major incidents.
The first time you run Checkov on existing infrastructure code, you'll probably get overwhelmed by the number of issues it finds. Don't panic, most teams have hundreds of minor security issues they never knew about.
What it catches:
S3 buckets that are accidentally public
Security groups that are too permissive
Unencrypted databases and storage
Missing backup configurations
Compliance violations across major frameworks
The learning curve:
Easy to install and run
Takes time to tune policies for your environment
Can generate false positives without proper configuration
Works best when integrated into CI/CD from the start
Why it's essential
Because the security issue you don't know about is the one that will bite you.
Getting started
pip install checkov and run it on your existing code. Prepare to learn things you didn't want to know about your infrastructure.
Pricing
Free (Open source under Apache 2.0 license)
Spacelift

What it actually does
Makes multi-tool IaC management less painful
Why it matters
Because most teams use more than one IaC tool
Real talk
Enterprise-grade orchestration that actually works
Here's something nobody talks about: managing multiple IaC tools across teams is harder than the tools themselves.
Spacelift brings sanity to environments where some teams use Terraform, others use Pulumi, and everyone’s trying to coordinate deployments.
Half of Spacelift’s deployments are now running OpenTofu, which tells you something about where the market is heading.
What it solves:
Coordinating deployments across multiple IaC tools
Policy enforcement that actually gets followed
Drift detection that doesn't generate noise
Approval workflows that don't slow teams down
When you need it:
Multiple teams with different IaC preferences
Complex environments with dependencies between stacks
Enterprise governance and compliance requirements
More than a handful of people managing infrastructure
The trade-offs:
Commercial platform with real costs
Learning curve for workflow configuration
Probably overkill for small teams
Worth it when coordination becomes a problem
Getting started
Free tier lets you test with real workloads. Their onboarding actually explains how to organize complex environments.
Pricing
Free tier available, Starter plan at $250/month, Starter+ and Business plans (annual), Enterprise (custom pricing)
Infrastructure Provisioning: The Tools That Build Things
Once your reviews are solid, you still need reliable ways to actually spin up infrastructure. These provisioning tools are what turn code into running systems.
OpenTofu

What it actually does
Terraform without the vendor lock-in anxiety
Why it matters
Because depending on one company for critical infrastructure is risky
Real talk
This is where smart teams are heading
Remember when HashiCorp changed Terraform’s license and everyone freaked out? The community didn’t just complain, they built something better.
OpenTofu isn’t just a Terraform fork; it’s proof that community-driven development can outpace corporate priorities. Fidelity recently announced they’re switching to OpenTofu as their default IaC platform. When a financial giant publicly ditches Terraform, that’s not news, that’s a signal.
Why teams are switching:
Same syntax and providers as Terraform, but actually open source
Features Terraform users requested for years (like state encryption)
Linux Foundation governance means no surprise license changes
Growing faster than anyone expected
What you get:
Drop-in replacement for Terraform
Built-in state encryption (finally!)
Early variable evaluation that actually works
Dynamic providers for complex scenarios
The honest assessment:
Newer project with smaller ecosystem (but growing fast)
Some tooling still catching up to Terraform support
Feature development sometimes lags HashiCorp's resources
Worth the switch for long-term peace of mind
Migration reality:
If you're using Terraform 1.6 or earlier, migration is straightforward. Their docs include step-by-step guides that actually work.
Getting started
Start with a non-critical project and migrate gradually. Most teams are surprised how smooth the transition is.
Pricing
Free (Open source under Mozilla Public License 2.0)
5. Terraform

What it actually does
The infrastructure tool everyone knows
Why it still matters
Massive ecosystem and proven track record
Real talk
Still good, but the license situation is awkward
Terraform is the 800-pound gorilla of IaC. It’s battle-tested, well-documented, and has solutions for pretty much every infrastructure problem you can imagine. The Business Source License situation creates some uncertainty, but it's not going anywhere soon.
Why it's still relevant:
Largest ecosystem with 3,900+ providers
Proven at massive scale (Netflix, Uber, etc.)
Most comprehensive third-party tooling
Best documentation and learning resources
The license reality:
BSL allows most common use cases
Creates uncertainty for some commercial scenarios
Risk of future restrictions or changes
Some teams switching to OpenTofu as insurance
When to stick with Terraform:
Heavily invested in HashiCorp ecosystem
Using enterprise features not available elsewhere
Need maximum provider and tooling compatibility
Comfortable with license terms
The honest take:
Still a solid choice if the license terms work for your organization. Just have an exit strategy
Getting started
HashiCorp Learn platform has excellent free tutorials.
Pricing
Free (Community edition), Terraform Cloud has free tier, Standard and Plus plans (RUM-based pricing) varies.
6. Pulumi

What it actually does
Infrastructure code using real programming languages
Why developers love it:
Because DSLs are annoying
Real talk:
Game-changer for teams that think in code
While everyone else argues about YAML vs HCL, Pulumi lets you use actual programming languages. Python, TypeScript, Go, C#, if you can code in it, you can manage infrastructure with it. This isn’t just convenience. Real programming languages mean real programming constructs: loops, conditionals, functions, classes, and all the abstractions that make complex systems manageable.
Why it's different:
Use languages your team already knows
Actual programming constructs (loops, functions, classes)
Superior testing and debugging capabilities
Native package manager integration
Who should use it:
Developer-heavy teams tired of learning DSLs
Complex infrastructure requiring dynamic logic
Teams that want to test infrastructure code properly
Organizations standardizing on specific languages
The trade-offs:
Learning curve for traditional ops teams
Smaller ecosystem than Terraform/OpenTofu
Risk of over-engineering infrastructure
Can be overkill for simple deployments
Getting started:
Pick your favorite language and follow their guides. The Python tutorial is particularly good for infrastructure beginners.
Pricing
Free for individuals, Team edition at $0.0005 per Pulumi Credit (resource-hour), Enterprise starts at ~$32,850/year, Business Critical starts at ~$50,000/year
7. AWS CloudFormation

What it actually does
AWS infrastructure the Amazon way. Deepest AWS integration possible
Real talk
Perfect for AWS-only shops, painful for everyone else
If you're all-in on AWS and plan to stay that way, CloudFormation gives you the deepest possible integration. New AWS services often show up in CloudFormation before the APIs are fully documented.
The AWS advantage:
Immediate support for new AWS services
No external state management headaches
Direct AWS support when things break
Best integration with AWS governance tools
The reality check:
AWS-only means no multi-cloud flexibility
YAML/JSON syntax gets ugly fast
Limited reusability compared to modern tools
Can't use the same skills elsewhere
When it makes sense:
Committed to AWS long-term
Need immediate access to new AWS features
Want direct AWS support for infrastructure issues
Prefer vendor-managed solutions
Getting started:
AWS documentation is comprehensive. The CloudFormation Designer helps visualize complex templates.
Pricing
Free (AWS service - you only pay for the AWS resources created)
8. Azure Bicep

What it actually does
ARM templates that don't make you cry
Why it exists
Because nobody likes JSON hell
Real talk
What ARM templates should have been from the start
Microsoft looked at ARM templates, saw the mess they created, and built Bicep to fix it. Same functionality, readable syntax, and tooling that doesn't fight you.
Why it's better than ARM:
Human-readable syntax instead of JSON nightmare
Strong typing prevents stupid mistakes
Excellent VS Code integration
Compiles to ARM so it's not a separate platform
The limitations:
Still Azure-only
Smaller community than multi-cloud tools
Limited third-party tooling
Need to learn Microsoft's way of thinking
When to choose it:
Azure-focused organization
Migrating from ARM templates
Want modern tooling for Azure infrastructure
Prefer Microsoft's ecosystem
Getting started:
Microsoft Learn modules are actually good. The playground environments let you experiment safely.
Pricing
Free (Open source, compiles to ARM templates)
Configuration Management: Making Servers Do What You Want
Provisioning gets your infra up, but someone still has to keep those servers in line. That’s where configuration management comes in, tools built to make servers actually do what you want, consistently
9. Ansible

What it actually does
Configuration management that doesn't require a PhD
Why it's popular
No agents, readable YAML, just works
Real talk
The Swiss Army knife of automation
Ansible is what happens when someone builds automation tools for normal humans. No agents to manage, readable playbooks, and it works on pretty much everything.
Why teams love it:
No software to install on target systems
YAML that humans can actually read
Works for both config management and infrastructure provisioning
Huge library of pre-built modules
Where it struggles:
Performance isn't great for large deployments
State management is messy compared to other tools
Can get complex with dependencies
Not ideal for infrastructure-heavy workloads
Best use cases:
Hybrid environments with diverse systems
Teams that need both config and infrastructure automation
Organizations that want simple, understandable automation
Environments where agents aren't practical
Getting started:
Community documentation is excellent. Red Hat's training materials are worth the investment.
Pricing
Free (Open source under GPL license)
10. Chef

What it actually does:
Enterprise-grade configuration management
Why enterprises use it:
Compliance and policy enforcement that actually works
Real talk:
Powerful but complex
Chef is the tool you use when configuration management is serious business. It’s Ruby-based, test-driven, and designed for environments where compliance isn’t optional.
Enterprise strengths:
Robust testing framework for infrastructure
Comprehensive compliance and audit capabilities
Detailed reporting and audit capabilities
Mature ecosystem for complex environments
The complexity cost:
Steep learning curve requiring Ruby skills
Complex architecture with multiple moving parts
Higher overhead than simpler alternatives
Can be overkill for straightforward needs
When it makes sense:
Large, complex environments
Strict compliance requirements
Teams with Ruby expertise
Organizations that need comprehensive reporting
Getting started:
Progress Chef's training programs are comprehensive. Community cookbooks provide good starting points.
Pricing
Free tier available, Commercial plans start around $189/node/year (contact for enterprise pricing)
11. Puppet

What it actually does:
Keeps thousands of systems in line
Why it's still relevant:
State management at scale
Real talk:
Old but reliable
Puppet has been around forever in infrastructure terms, but it’s still relevant because it solves state management really well across large environments.
What it does well:
Manages desired state across thousands of systems
Automatic dependency resolution
Comprehensive reporting on system state
Mature ecosystem with extensive modules
The operational reality:
Complex setup and ongoing maintenance
Resource-intensive master/agent architecture
Learning curve for Puppet's DSL
Can be overwhelming for smaller environments
Best fit scenarios:
Large environments requiring state consistency
Teams with existing Puppet expertise
Organizations needing detailed compliance reporting
Environments where centralized control is important
Getting started:
Puppet Education provides structured paths. Puppet Forge has modules for common scenarios.
Pricing
Free (Open source version), Enterprise pricing varies (contact for quote)
Kubernetes and Cloud-Native Tools
For teams living and breathing Kubernetes, the next step is managing infrastructure the same way you manage pods and services. These cloud-native tools extend Kubernetes into a universal control plane.
12. Crossplane

What it actually does:
Kubernetes-native infrastructure management
Why it matters:
Everything-through-Kubernetes approach
Real talk:
Complex but powerful for Kubernetes-centric orgs
If your world revolves around Kubernetes, Crossplane turns your cluster into a universal control plane for infrastructure. It’s not simple, but it unifies how you manage everything.
The Kubernetes advantage:
Manage infrastructure using familiar Kubernetes patterns
Strong GitOps integration
Unified APIs across cloud providers
Perfect for platform engineering approaches
The complexity trade-off:
Requires deep Kubernetes knowledge
Complex setup and operations
Limited value outside Kubernetes environments
Steep learning curve for traditional infrastructure teams
When it makes sense:
Kubernetes-centric organization
Platform engineering initiatives
Teams already deep in cloud-native patterns
Need for unified infrastructure APIs
Getting started:
CNCF docs are comprehensive. Start with simple examples before attempting complex compositions.
Pricing
Free (Open source under Apache 2.0 license)
13. AWS CDK

What it actually does
AWS infrastructure using real programming languages
Why developers like it
Familiar syntax, deep AWS integration
Real talk
Great for AWS, vendor lock-in for everything else
AWS CDK lets you define infrastructure using the same languages you use for applications. It's not just convenience, it's a fundamentally different approach to infrastructure definition.
Developer benefits:
Use languages your team already knows
Excellent IDE support and debugging
Strong typing prevents configuration errors
Natural patterns for complex logic
The AWS reality:
Deep integration with AWS services
Vendor lock-in by design
Can't easily migrate to other clouds
AWS-specific patterns and constructs
Best scenarios:
AWS-committed organizations
Developer-heavy teams
Complex infrastructure requiring programming logic
Teams wanting modern development patterns
Getting started
AWS workshops are well-designed. Language-specific guides provide good starting points.
Pricing
Free (AWS service – you only pay for the underlying AWS resources)
Security and Specialized Tools
Even with the best provisioning and config tools, none of it matters if your stack isn’t secure. These security and specialized tools help you catch the vulnerabilities hiding in plain sight.
14. Trivy

What it actually does:
Finds vulnerabilities in everything
Why security teams like it:
Comprehensive scanning that actually works
Real talk:
Essential for container and infrastructure security
Trivy scans containers, filesystems, Git repositories, and infrastructure code for vulnerabilities and misconfigurations. It's fast, accurate, and finds things that matter.
Comprehensive coverage:
Container image vulnerabilities
Infrastructure code misconfigurations
Filesystem and dependency scanning
Secret detection in code repositories
Why it's practical:
Fast scanning with minimal false positives
Easy CI/CD integration
Constantly updated vulnerability database
Works well in automated workflows
Integration reality:
Simple to set up and use
Can generate noise without proper filtering
Requires workflow integration for maximum value
Works best as part of comprehensive security strategy
Getting started:
Installation is simple. CI/CD examples help with workflow integration.
Pricing
Free (Open source under Apache 2.0 license)
15. env0

What it actually does:
IaC automation with cost focus
Why finance teams like it:
Actual cost visibility and control
Real talk:
Good for teams serious about cloud spend
env0 provides automation and governance for multiple IaC tools, with strong emphasis on cost optimization and financial operations.
Cost management strengths:
Detailed cost estimation before deployment
Policy enforcement around spending
Multi-cloud cost optimization
Integration with FinOps workflows
Platform capabilities:
Support for multiple IaC tools
Workflow automation and governance
Policy enforcement and compliance
Cost tracking and optimization
Commercial considerations:
Pricing reflects enterprise focus
Learning curve for policy configuration
May be overkill for cost-insensitive environments
Best value for teams with complex cost requirements
Getting started:
Free tier provides good evaluation capabilities. Cost optimization guides are practical.
Pricing
Free tier available, paid plans start around $399/month (contact for enterprise pricing)
16. DNSControl

What it actually does:
DNS management that doesn't suck
Why it matters:
Because DNS outages take down everything
Real talk:
Simple tool that solves a specific problem well
DNS management through web interfaces is terrible. DNSControl treats DNS like code, with version control, testing, and automation for critical infrastructure.
Why it's essential:
Version control for DNS changes
Testing and validation before deployment
Multi-provider management from single source
Automation for complex DNS scenarios
Simplicity advantage:
Focused on DNS, does it well
Clear syntax for DNS records
Good provider support
Straightforward to learn and use
Scope limitations:
Only handles DNS use cases
Smaller community than general tools
Requires DNS knowledge for complex setups
Limited to DNS automation scenarios
Getting started:
Documentation includes practical examples. Migration guides help move from existing DNS setups.
Pricing
Free (Open source under MIT License)
Building an IaC Strategy That Actually Works
The tools matter, but strategy matters more. Here's how to build infrastructure automation that doesn't create more problems than it solves:
Start with the Pain Points
Fix Code Review First Most teams are still reviewing infrastructure code manually. Tools like CodeAnt AI solve the fundamental scalability problem with infrastructure review. Start here before optimizing other parts of the workflow.
Address Security Early Security scanning with tools like Checkov should be part of your workflow from day one, not bolted on later. The cost of implementing security review early is nothing compared to cleaning up after a breach.
Plan for Complexity Most organizations end up with multiple IaC tools. Tools like Spacelift become essential once you have more than one team or more than one tool in production.
Match Tools to Reality
Team Skills Trump Features Choose tools your team can actually use effectively. Pulumi makes sense for development teams. OpenTofu/Terraform work for mixed teams. Ansible fits operations-focused environments.
Cloud Strategy Determines Tools Single cloud? Use native tools for deepest integration. Multi-cloud? Stick with community standards like OpenTofu. Kubernetes-focused? Consider cloud-native approaches like Crossplane.
Size Affects Everything Small teams need tools that just work. Large organizations need governance, policy enforcement, and coordination capabilities. Don't over-engineer for scale you don't have.
Avoid Common Mistakes
Don't Try to Standardize Everything Different teams have different needs. Forcing everyone onto the same tool often creates more problems than it solves.
Security Isn't Optional 73% of enterprises had AI-related security incidents last year. Security review and scanning need to be built into workflows, not added later.
Plan for Change The Terraform licensing situation showed that depending on a single vendor for critical tools is risky. Choose tools and strategies that give you options.
The Real Talk Summary
Infrastructure as Code in 2025 isn't about choosing the "best" tool, it's about building workflows that scale with your team and protect against the risks that come with rapid, AI-assisted development.
What's actually changed in 2025:
AI-powered code review has become essential, not optional
OpenTofu's momentum is real, 20% of new projects start there
Security scanning needs to be built into workflows from the start
Multi-tool orchestration platforms solve real coordination problems
What hasn't changed:
Team skills matter more than tool features
Simple solutions beat complex ones for most use cases
Security bolted on later doesn't work
Tool choices should align with cloud strategy
The bottom line: Start with tools that solve your biggest pain points first. For most teams in 2025, that means intelligent code review, comprehensive security scanning, and infrastructure provisioning that doesn't lock you into a single vendor's roadmap.
The Bottom Line: Choose Tools That Actually Work Together
After diving into 16 different IaC tools, here's what matters most: your infrastructure is only as secure as your weakest review process. You can have the best provisioning tools in the world, but if you're missing critical security issues during code review, you're setting yourself up for expensive problems later.
The smart teams we see aren't just picking one perfect tool—they're building workflows where security, provisioning, and configuration management actually work together. They're using AI to catch what manual reviews miss, choosing open-source tools like OpenTofu for long-term flexibility, and implementing comprehensive scanning before anything hits production.
Start with what's broken first. For most teams, that's the one that never happens.
Ready to see what intelligent infrastructure code review looks like? Try CodeAnt AI free for 14 days and watch it catch the security issues your team would otherwise miss. No setup headaches, no credit card required, just connect your repo and see the difference AI-powered review makes.
Because the best infrastructure security incident is the one that never happens.
FAQs
What should an Infrastructure as Code review checklist include?
Terraform vs OpenTofu in 2025, which should my team use?
How do I secure Terraform and Kubernetes IaC in CI/CD?
What metrics prove my IaC process is safe and fast?
How do AI tools like CodeAnt AI reduce IaC risk in real life?
Table of Contents
Start Your 14-Day Free Trial
AI code reviews, security, and quality trusted by modern engineering teams. No credit card required!
Share blog:















