AI Code Security
Code Security Build for the AI Era
SAST. Secrets. IaC. SCA. SBOM. CSMP. One platform that never blinks.
Trusted by Startups to Fortune 500





















Features
Building Blocks For Secure Development
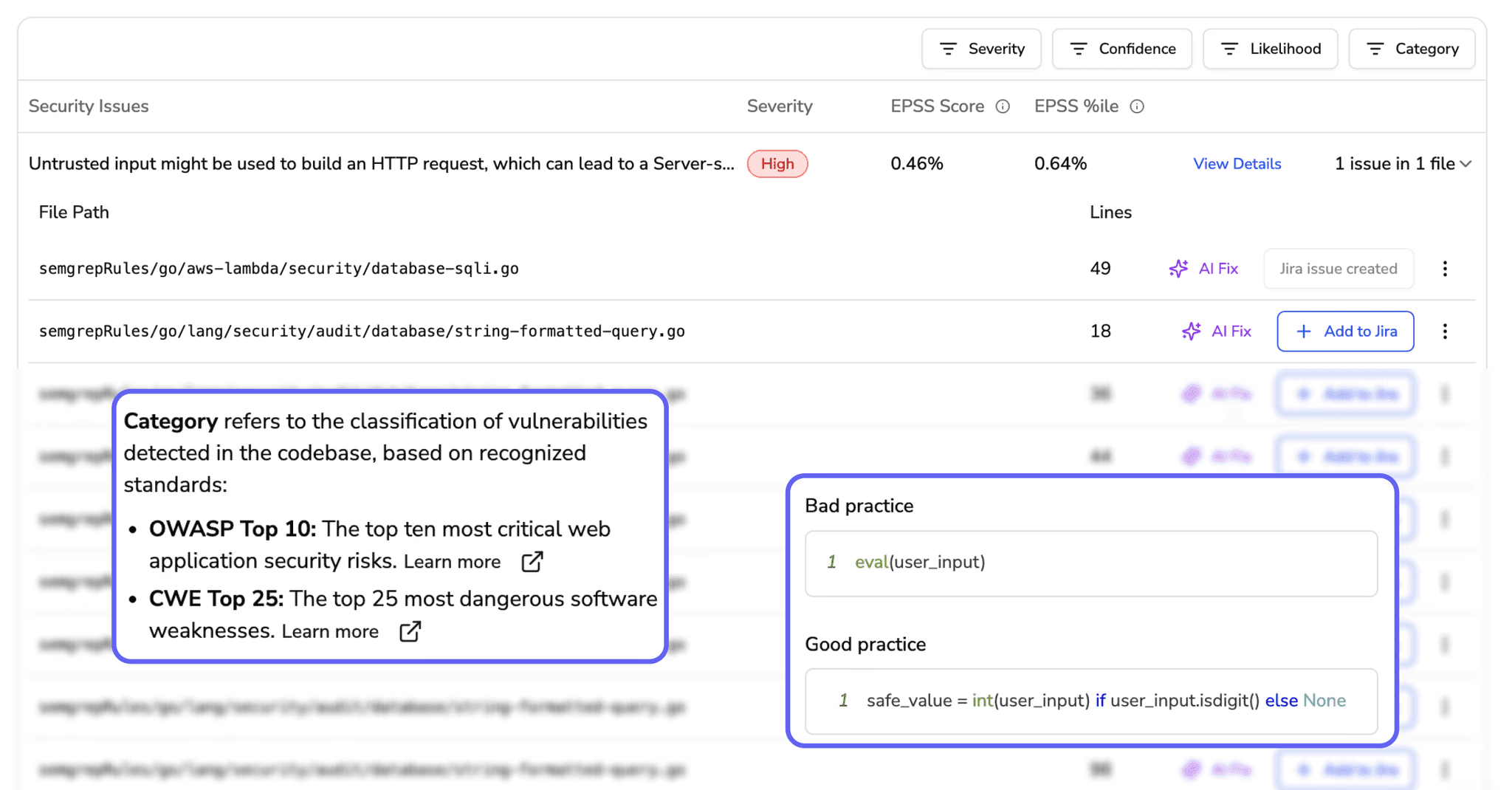
SAST
Find security issues before code ships
IaC
Cloud Misconfig
SCA
Secrets
EPSS
Security Dashboard
SBOM
SAST
Find security issues before code ships

IaC
Cloud Misconfig
SCA
Secrets
EPSS
Security Dashboard
SBOM
SAST
Find security issues before code ships

IaC
Cloud Misconfig
SCA
Secrets
EPSS
Security Dashboard
SBOM
SAST
IaC
Cloud Misconfig
SCA
Secrets
EPSS
Security Dashboard
SBOM

Detect common and critical security flaws early.
Issues are caught during review, not after release.
How CodeAnt Leaves Legacy SAST Behind
With Legacy Tools
With Legacy Tools
With CodeAnt AI
With CodeAnt AI
Lacks context awareness
Lacks context awareness
Learns from every Pull Request & repo
Learns from every Pull Request & repo
70–80% false positives
70–80% false positives
Less than 5% false positives
Less than 5% false positives
30–60 min runtime
30–60 min runtime
< 60 seconds per Pull Request
< 60 seconds per Pull Request
Limited to SAST only
Limited to SAST only
SAST + SCA + IaC + Secrets + SBOM
SAST + SCA + IaC + Secrets + SBOM
Real Results from Real Customers



Real Results from Real Customers



Real Results from Real Customers



FOR MANAGERS
Everything You Need To Govern Code Security
Security Reports
Generate compliance-friendly security reports instantly.
Security Gating
Enforce security checks automatically.
FAQs
How is CodeAnt AI different from legacy SAST tools?
How is CodeAnt AI different from legacy SAST tools?
How is CodeAnt AI different from legacy SAST tools?
Can I enforce compliance standards like SOC 2 or HIPAA?
Can I enforce compliance standards like SOC 2 or HIPAA?
Can I enforce compliance standards like SOC 2 or HIPAA?
Does CodeAnt AI support multi-repo, enterprise-scale setups?
Does CodeAnt AI support multi-repo, enterprise-scale setups?
Does CodeAnt AI support multi-repo, enterprise-scale setups?
What kind of IaC and cloud checks are included?
What kind of IaC and cloud checks are included?
What kind of IaC and cloud checks are included?
How do you handle open-source dependency risks?
How do you handle open-source dependency risks?
How do you handle open-source dependency risks?
How is secret scanning different from GitHub’s?
How is secret scanning different from GitHub’s?
How is secret scanning different from GitHub’s?
Can I block merges if vulnerabilities are found?
Can I block merges if vulnerabilities are found?
Can I block merges if vulnerabilities are found?