Security Reporting
Turn Security Data Into Business Insight
Move beyond raw issue lists. CodeAnt AI generates structured security reports mapped to compliance frameworks and remediation progress.
CodeAnt scans every PR for security risks — injection, config, or API — and suggests fixes using real-time SAST.
CodeAnt scans every PR for security risks — injection, config, or API — and suggests fixes using real-time SAST.
Trusted by Enterprises
Trusted by Enterprises
Trusted by Enterprises
A Single View of Risk Across Your Organization
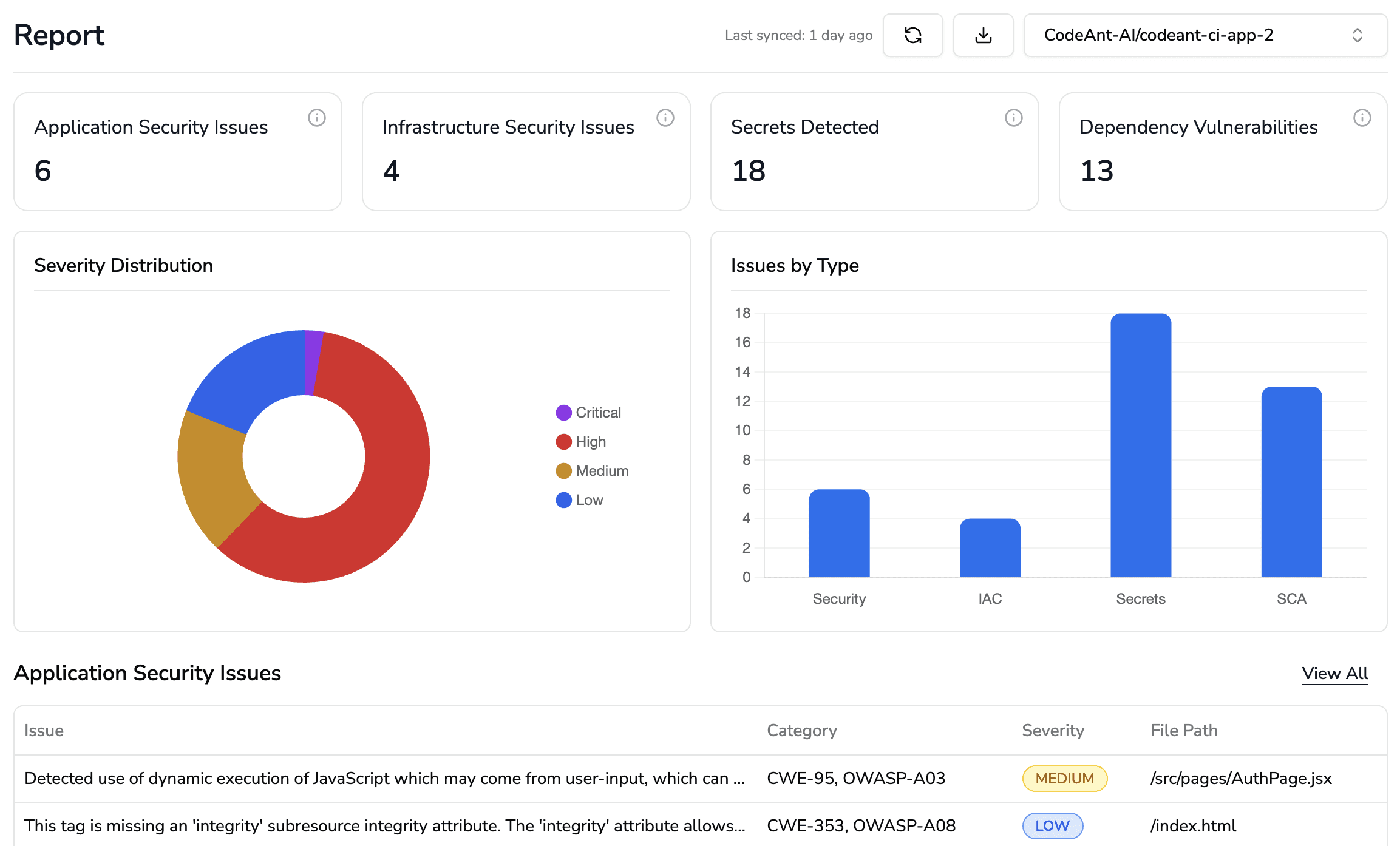


Centralized security posture
Aggregate application, infrastructure, secrets, and dependency risks across repositories to understand org-wide exposure at a glance.
Prioritize what matters most
Severity trends and issue distribution help security leaders focus remediation where risk is highest.
Why Best Teams Love CodeAnt AI

NASDAQ:CVLT ($8 Billion Market Cap)
How CodeAnt’s Code Health Platform Powers Commvault’s 800+ Developers

NASDAQ:CVLT ($8 Billion Market Cap)
How CodeAnt’s Code Health Platform Powers Commvault’s 800+ Developers

NASDAQ:CVLT ($8 Billion Market Cap)
How CodeAnt’s Code Health Platform Powers Commvault’s 800+ Developers
From Security Findings to Boardroom Decisions
From Security Findings to Boardroom Decisions
From Security Findings to Boardroom Decisions
FAQs
How fast can I get started with CodeAnt AI?
How fast can I get started with CodeAnt AI?
How fast can I get started with CodeAnt AI?
Do you support GitHub, GitLab, Bitbucket, and Azure DevOps?
Do you support GitHub, GitLab, Bitbucket, and Azure DevOps?
Do you support GitHub, GitLab, Bitbucket, and Azure DevOps?
Can I enforce custom rules for my team’s codebase?
Can I enforce custom rules for my team’s codebase?
Can I enforce custom rules for my team’s codebase?
How is this different from GitHub Copilot’s code suggestions?
How is this different from GitHub Copilot’s code suggestions?
How is this different from GitHub Copilot’s code suggestions?
What happens after the 14-day trial?
What happens after the 14-day trial?
What happens after the 14-day trial?
Can I try just the AI Code Review product?
Can I try just the AI Code Review product?
Can I try just the AI Code Review product?
Is my code data retained or used to train your models?
Is my code data retained or used to train your models?
Is my code data retained or used to train your models?
How do you handle secrets and security scanning?
How do you handle secrets and security scanning?
How do you handle secrets and security scanning?




























