AI Code Review
Feb 6, 2026
How to Roll Out AI Code Review Without Slowing PRs

Sonali Sood
Founding GTM, CodeAnt AI
You've seen it happen: an AI code review tool launches Monday morning, and by Wednesday, developers are Slacking each other's workarounds to bypass it. The tool flags hundreds of issues, most irrelevant. PRs that used to merge in hours now sit for days. Within two weeks, adoption craters.
The problem isn't AI code review itself, it's treating rollout like flipping a switch. Successful teams deploy AI code review through a deliberate, phased approach that builds trust before demanding compliance.
This guide walks through the exact framework high-performing engineering teams use: from selecting pilot repos and proving ROI in two weeks, to expanding organization-wide without triggering developer revolt.
Why Most AI Code Review Rollouts Fail
AI code review rollouts fail when teams treat them like infrastructure deployments instead of workflow transformations. The pattern is consistent: evaluate a tool, run a proof-of-concept, enable it across all repos simultaneously. Within two weeks, developers are filing tickets to disable it.
The Disruption Trap
Big-bang enablement creates immediate friction
Turning on AI review across 200+ repositories simultaneously means every team experiences disruption at once, with no champions to demonstrate value. When developers encounter their first false positive, there's no one who's seen the benefit to vouch for the tool.
PR comment spam destroys signal-to-noise ratio
Tools configured to flag every potential issue generate 40–60 comments per pull request, burying the 3–4 legitimate concerns that matter. One team saw SonarQube generate 127 comments on a routine refactoring PR, the developer stopped reading after 15.
False positives erode trust faster than true positives build it
A 30–40% false positive rate, common with pattern-matching tools lacking codebase context, means developers waste 2–3 hours per week investigating irrelevant findings. After two sprints, they stop trusting the tool entirely.
Blocking policies too early kill momentum
Requiring AI approval before merge when the tool is still learning your codebase slows deployment velocity by 40–50%. Developers shipping 3–4 PRs daily are suddenly stuck waiting for AI approval on changes they know are safe.
The Hidden Cost
Context switching from low-quality feedback costs teams 20–30% of effective working time. When AI interrupts flow with bad suggestions, developers lose 15–20 minutes recovering their mental model.
For 100 developers receiving 3–4 false positives daily, that's 250–300 hours per week investigating and dismissing bad suggestions, equivalent to 6–7 full-time engineers.
The downstream effects compound:
Review cycles balloon from 2 rounds to 4–5 rounds
PR merge time increases from 13 hours to 2+ days
Developer satisfaction drops 35–40 points
One fintech team calculated their previous AI tool cost $180K annually in lost productivity, not counting delayed features.
The 3-Phase Rollout Framework: Pilot → Team → Organization
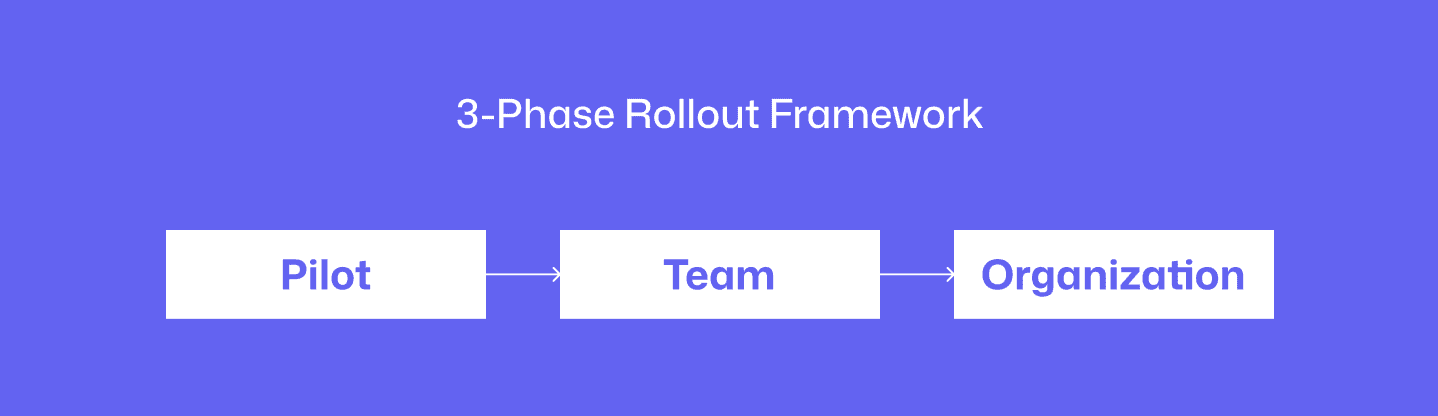
Successful AI code review adoption builds trust, proves value, and scales governance deliberately. This framework minimizes disruption by starting small with senior advocates, expanding with feedback-driven customization, and scaling with enterprise controls that don't block developers.
Phase Progression
Phase 1: Pilot (Weeks 1-2)
Scope: 1-2 high-velocity repositories, 3-5 senior developers
Mode: Observation only—no blocking, no mandates
Goal: Prove 40% faster review cycles, capture actionable feedback
Gate: Senior developers report time savings and recommend expansion
Phase 2: Team Expansion (Weeks 3-6)
Scope: Full team (10-30 developers), 5-10 repositories
Mode: Advisory suggestions with opt-in auto-fixes
Goal: 80% team adoption, <10% false positive rate
Gate: Weekly NPS >70, measurable reduction in review round-trips
Phase 3: Organization Rollout (Weeks 7-12)
Scope: All teams, 50+ repositories
Mode: Policy enforcement with escape hatches
Goal: Standardized governance, 35% deployment frequency increase
Gate: Executive sign-off on ROI metrics and change failure rate reduction
What You Deliberately Avoid Early
No hard blocking in Weeks 1-6: AI runs in advisory mode, surfacing issues without failing builds
No org-wide mandates before Week 7: Let early adopters become internal advocates
No configuration marathons: Context-aware AI learns your codebase patterns automatically
No "all or nothing" scans: Start with high-signal checks (secrets, critical vulnerabilities)
Phase 1: Prove Value with Senior Advocates (Weeks 1-2)
The pilot phase determines whether AI code review lives or dies. You're building the internal case for adoption and proving measurable impact before asking 50+ developers to change workflow.
Week 1: Select Repos and Champions Strategically
Choose pilot repositories carefully:
High PR volume (10+ per week): Generate statistically meaningful data
Active ownership: Engaged maintainers who respond to suggestions
Representative risk profile: Include repos handling sensitive data
Moderate complexity: Avoid trivial services or legacy monoliths
For 100+ developers, 2–3 repos is optimal.
Recruit 3–5 senior engineers plus one security partner who:
Embrace tooling and understand automation ROI
Can articulate value to skeptics
Represent different disciplines (backend, frontend, infrastructure)
Frame this as a two-week experiment with a go/no-go gate.
Establish Baseline Metrics
Measure current state before enabling AI. Track across pilot repos:
Metric | Baseline Target |
PR cycle time | 13–18 hours median |
Review iterations | 2.5–3 rounds per PR |
PR reopen rate | 8–12% |
Escaped vulnerabilities | 3–5 per quarter |
These give you concrete targets. If CodeAnt AI doesn't move the needle on at least two metrics, the pilot hasn't proven value.
Week 1–2: Integrate and Configure
Connect CodeAnt to VCS and CI in under 30 minutes:
Enable narrow check categories first:
Security-critical findings: SQL injection, XSS, hardcoded secrets
High-confidence quality issues: Unused variables, unreachable code
Disable broader quality rules (complexity, duplication) during pilot. You're building trust first.
Set Noise Budget and Feedback Loop
Track false-positive rate religiously. Developers abandon tools above 15% FP rate.
Create a #codeant-pilot Slack channel for champions to flag:
False positives to tune
Missed issues AI should catch
Workflow friction
Review feedback daily during Week 2. Rapid iteration signals developers their input matters.
The Go/No-Go Gate
End of Week 2, evaluate against two hard criteria:
1. Measurable improvement on at least two metrics:
Target: 30–40% reduction in PR cycle time (13h → 8h)
Target: 20–30% reduction in review iterations (2.8 → 2.0 rounds)
Target: 2–3 legitimate security issues caught
2. Acceptable false-positive rate and champion advocacy:
Target: <12% false-positive rate
Target: At least 4 of 5 champions recommend expansion
If champions are frustrated by noise, pause and tune rather than pushing forward. A failed Phase 2 rollout is far more expensive than extending the pilot.
Phase 2: Team Expansion with Scoped Controls (Weeks 3-6)
Once your pilot proves value, expand to a full team without triggering alert fatigue. This phase introduces progressive policies, rapid tuning, and developer trust through transparent calibration.
Progressive Gating
Don't flip everything to blocking overnight. Use CodeAnt's repo-level controls:
Week 3: Comment-only for all new repos
Enable AI across target team's repositories with all findings as informational comments only.
Week 4: Soft gates for high-severity security
Block only critical/high security findings. Leave quality as guidance.
Week 5–6: Quality gates for high-complexity changes
Expand blocking to quality issues in high-risk areas.
Streamlined Onboarding
15-minute setup flow:
Slack announcement with video (5 min): Show real PR with before/after review cycles
IDE integration (5 min): Install CodeAnt plugin, authenticate via SSO
First PR with AI review (5 min): Submit small change, see comments, accept one auto-fix
One-page cheat sheet covering:
What AI checks run on every PR
How to suppress false positives (
// codeant-ignore: rule-id)When to escalate issues
Who owns calibration
Tune Rules in Hours, Not Weeks
Suppression patterns for common false positives:
CODEOWNERS alignment:
CodeAnt routes findings to the right teams automatically. Security issues in auth/ notify @security-team, not the PR author.
Weekly Calibration Cadence
30-minute weekly sync with team lead, 2–3 developers, and a CodeAnt champion:
Review top false positives (10 min): Decide to tune, suppress, or keep
Highlight valuable catches (10 min): Share examples where AI prevented bugs
Adjust policy for next week (10 min): Expand or dial back based on feedback
Publish changes transparently in Slack after each session.
By Week 6, expect:
<10% false positive rate (down from 20–30% in Week 3)
60% reduction in review round-trips
Zero blocking PRs for >2 hours
Phase 3: Organization Rollout with Governance (Weeks 7-12)
By Phase 3, the question is no longer “Will developers accept AI code review?”
It’s “Where should AI be strict, and where should it stay advisory?”
Organizations fail at this stage when they apply uniform enforcement across non-uniform systems. A payments service that breaks production twice a quarter should not be treated the same as a stable internal tooling repo that hasn’t caused an incident in a year.
Phase 3 is about calibrating AI enforcement based on real production risk, not rolling out the same gates everywhere.
The Shift in Mindset
Earlier phases focus on trust and adoption. Phase 3 focuses on optimization.
You stop asking:
“Should AI block merges?”
And start asking:
“Where does AI blocking actually reduce incidents?”
“Which repos need stricter scrutiny, and which don’t?”
“How do we tune enforcement without slowing the entire organization?”
This is where AI code review becomes a governance system, not just a reviewer.
Step 1: Classify Repositories by Production Risk
Before expanding enforcement, segment repositories using observed operational behavior, not labels like “critical” or “non-critical.”
Common classification signals:
Production incident frequency (last 90–180 days)
Rollback rate or hotfix frequency
Change failure rate (from DORA metrics)
Ownership clarity (single team vs. shared)
Surface area (auth, payments, data access, infra)
Example risk tiers:
Repo Tier | Characteristics | Enforcement Strategy |
Tier 1 – High Risk | Frequent incidents, customer-impacting | Strict AI gates |
Tier 2 – Medium Risk | Occasional regressions | Selective blocking |
Tier 3 – Low Risk | Stable, internal, low blast radius | Advisory only |
This classification should evolve quarterly. Repos move between tiers.
Step 2: Experiment with Enforcement Thresholds per Tier
Instead of a single org-wide policy, Phase 3 introduces controlled experimentation.
Each tier gets different AI behavior, tuned to risk tolerance.
Tier 1: High-Risk Repositories
Block merges on:
Security vulnerabilities
Authorization/authentication changes
Data access logic regressions
Enable deeper AI analysis:
Cross-repo context
Historical incident correlation
Require explicit override justification
Outcome: Fewer production incidents, slower but safer merges.
Tier 2: Medium-Risk Repositories
Block only on:
Critical security findings
Warn (don’t block) on:
Complexity spikes
Performance regressions
Auto-fix allowed for low-risk issues
Outcome: Improved quality without merge friction.
Tier 3: Low-Risk Repositories
No blocking
Comment-only AI feedback
Auto-apply formatting, cleanup, and safe refactors
Outcome: Faster merges and developer leverage, not control.
Step 3: Use Production Feedback to Tune AI Strictness
Phase 3 introduces a closed feedback loop between production behavior and AI enforcement.
Every 2–4 weeks, review:
Which repos triggered incidents?
Which repos had AI-flagged issues that were overridden?
Where did AI blocking prevent regressions?
Then adjust:
Severity thresholds
Blocking rules
Auto-fix permissions
Example:
A repo with repeated post-merge incidents moves from Tier 2 → Tier 1
A stable repo with low override rates moves from Tier 2 → Tier 3
A noisy rule causing >15% overrides is downgraded or disabled
This keeps AI enforcement dynamic, not frozen.
Step 4: Roll Out Gradually, Not Universally
Instead of “all repos, same day,” Phase 3 expands in waves:
Weeks 7–8: High-risk repos only (Tier 1)
Weeks 9–10: Medium-risk repos (Tier 2)
Weeks 11–12: Remaining low-risk repos (Tier 3)
Each wave validates:
Merge time impact
Override rates
Incident correlation
If friction spikes, pause and recalibrate before expanding further.
What Success Looks Like by Week 12
By the end of Phase 3, teams typically see:
Strict AI enforcement where it matters
Advisory AI where speed matters
No org-wide slowdown
Clear visibility into why a repo has stricter rules
AI stops being “that thing blocking my PR” and becomes: “The reason this repo hasn’t broken production in months.”
Why This Works
Phase 3 succeeds because it aligns AI strictness with real operational risk, not org charts or gut feeling.
Stable teams aren’t punished
Risky systems get the guardrails they need
Enforcement evolves as systems evolve
Developers understand why rules exist
At this point, AI code review is no longer a rollout, it’s infrastructure.
Overcoming Developer Resistance
Developer buy-in determines rollout success. Most objections stem from legitimate concerns about past tools, they're addressable with evidence.
"AI doesn't understand our code"
Response: Modern AI learns from your repository's history, not just generic rules.
Demo repository-aware learning: Show CodeAnt identifying patterns from past PRs
Contrast with static analysis: Compare SonarQube's 200+ warnings vs. CodeAnt's 8 actionable issues
Prove contextual understanding: Share a PR where CodeAnt caught a subtle production issue
Proof: Track false positive rate weekly. CodeAnt achieves <10% after 2–3 weeks, vs. 30–40% for rule-based tools.
"This will spam our PRs"
Response: Configure a noise budget from day one.
Start security-only: Flag only critical/high security issues initially
Show severity thresholds: Demonstrate 2 critical issues surfaced, 15 low-priority suggestions suppressed
Implement soft-gate policies: Advisory mode preserves developer autonomy
Proof: Set "no more than 3 AI comments per PR on average." Track and adjust during pilot.
"Security will block our deployments"
Response: Position AI as shift-left prevention, not compliance hammer.
Show the alternative: Recent vulnerability that made production because manual review missed it
Demonstrate policy transparency: Show exact rules, ownership, compliance mappings
Highlight auto-fix: One-click remediation eliminates toil
Proof: Establish "security SLA"—findings must include remediation guidance. Teams see 60% reduction in security review cycles.
"AI will replace human review"
Response: Frame AI as handling mechanical work so humans focus on high-value review.
Show time savings: 70% of review comments are about formatting/security basics AI catches instantly
Position as complementary to Copilot: AI validates AI-generated code before human review
Demonstrate enhanced mentorship: AI explanations teach junior developers the "why"
Proof: Survey after 4 weeks. Teams report 40% more time on architecture, 60% less on syntax/security.
"We already have SonarQube/Snyk"
Response: Demonstrate the integration gap CodeAnt fills.
Show fragmentation: Map current workflow across multiple dashboards
Demonstrate unified context: Single view with cross-issue correlation
Highlight AI advantages: Show logic errors static analysis misses
Proof: Run 2-week comparison. CodeAnt catches 30–40% more issues while reducing noise 50%.
Measuring Rollout Success
Track both leading indicators (early signals) and lagging indicators (business outcomes).
Leading Indicators
Adoption coverage:
Week 2: 10–15% (pilot repos)
Week 6: 40–50% (team expansion)
Week 12: 80%+ (org-wide)
Engagement rate (PRs with AI review):
Week 2: 60–70%
Week 6: 75–85%
Week 12: 90%+
False positive rate:
Week 2: <15%
Week 6: <10%
Week 12: <5%
Developer NPS:
Week 1: 20–40 (baseline)
Week 4: 50+ (early value)
Week 12: 70+ (indispensable)
Lagging Indicators
PR cycle time:
Baseline: 13–18 hours
Week 6: 8–10 hours (30–40% reduction)
Week 12: 4–6 hours (60–70% reduction)
Review iterations per PR:
Baseline: 2.5–3.5 iterations
Week 6: 1.8–2.2 iterations
Week 12: 1.2–1.5 iterations
Defect escape rate:
Baseline: 8–12%
Week 6: 5–7%
Week 12: 3–5%
DORA metrics:
Lead time: 20–30% reduction by Week 12
Deployment frequency: 15–25% increase
Change failure rate: 30–40% reduction
CodeAnt's analytics dashboard surfaces all metrics automatically—no custom instrumentation required.
Operational Guardrails
Cap Comments and Prioritize by Severity
Set a hard limit on AI comments per PR—typically 5–10. CodeAnt automatically ranks findings by severity and suppresses lower-priority items:
Exclude Generated Code
Disable checks that generate false positives >15% or that your team ignores:
Define Ownership Routing
Route findings to the right teams:
Safe Auto-Fix Rollout
Graduate auto-fix capabilities:
Phase 1 (Weeks 1–4): Propose fixes as patches in PR comments
Phase 2 (Weeks 5–8): Enable auto-fix for low-risk categories with approval
Phase 3 (Week 9+): Fully automated fixes for proven-safe rules
Conclusion: Trust-Building, Not Tool Deployment
Rolling out AI code review isn't a technical challenge, it's trust-building. The phased strategy, pilot with advocates, expand with customization, govern at scale, works because it proves value before enforcing compliance.
Your next steps:
Pick 1–2 pilot repos with high velocity and senior developers
Define noise budget: <10% false positive threshold
Baseline metrics: Review cycle time, PR iterations, deployment frequency
Schedule Week 2 go/no-go: If not seeing 30–40% faster reviews, pause and adjust
Teams that succeed treat AI code review as workflow transformation, not tool installation. They measure adoption velocity alongside business outcomes, iterate based on feedback, and choose platforms purpose-built for gradual rollouts.
Ready to stand up a pilot in 30 minutes?Book a 1:1 with our team to see how CodeAnt AI's unified platform handles review, security, and quality without disrupting developers. Orstart a 14-day trial to explore the dashboards tracking rollout success from day one.