AI Code Review
Feb 5, 2026
Which Developer Tools Vendor Has the Best Static and Dynamic Vulnerability Detection

Sonali Sood
Founding GTM, CodeAnt AI
Your security team runs Checkmarx. DevOps swears by Invicti. Developers ignore alerts from both because they're drowning in 200+ findings per PR, most false positives. You're paying for SonarQube, Snyk, and three other tools that don't talk to each other. Audit prep still takes eight weeks.
The question isn't which vendor has the best static and dynamic vulnerability detection, it's why you're still choosing between them. Modern teams shipping code daily can't afford tool sprawl, alert fatigue, and integration overhead from traditional point solutions.
This guide shows you what actually matters:
accuracy that eliminates false positives
speed that fits high-velocity pipelines
actionable context that helps developers fix issues in seconds
We'll compare how different platforms stack up against legacy tools, and why the best answer might be the one that makes you stop asking "static or dynamic?" altogether.
The Real Problem: Tool Sprawl Is Killing Your Security Program
Most engineering teams manage a patchwork of point solutions:
SonarQube for code quality
Snyk for dependencies
Checkmarx for SAST
Invicti for DAST
GitGuardian for secrets
Each tool generates its own alerts, uses its own severity scale, and requires its own integration work.
The hidden costs compound fast:
Triage overhead: Security teams spend 15+ hours per week manually correlating duplicate findings across tools. That SQL injection flagged by SAST might be the same issue DAST reports, but you won't know without manual investigation.
Alert fatigue: When 75% of findings are false positives or low-priority noise, developers start ignoring security alerts entirely. Traditional SAST tools generate 200+ findings per PR with 85% false positive rates.
Integration complexity: Each tool requires its own CI/CD configuration, authentication setup, and reporting pipeline. Onboarding a new repository means repeating this process across every tool.
Context switching costs: Developers toggle between 4–5 dashboards to understand a single security issue, losing 23 minutes of deep work time per interruption.
The architectural problem:
When vulnerability detection happens in silos, you miss the connections that matter.
Your SAST tool flags a SQL injection.
Your SCA tool reports a vulnerable dependency.
Your secret scanner finds an API key.
Are these three separate issues or three perspectives on one exploit path? Manual correlation becomes a full-time job.
What Actually Matters for Modern Engineering Teams
The traditional vendor comparison focuses on feature checklists. But that's table stakes. What separates leaders from legacy tools is how they fit into high-velocity workflows without creating bottlenecks.
Here's what "best" really means:
Accuracy over volume: Reducing false positives by 80% matters more than flagging 200 theoretical issues per PR. You need exploitable findings, not noise.
Speed that matches developer flow: Real-time feedback in the IDE or PR review beats a 30-minute CI scan that breaks context and slows merges.
Context-aware prioritization: Understanding which vulnerabilities are reachable in production, which dependencies are actively exploited, and which secrets are exposed, not just pattern-matched strings.
Unified visibility: A single dashboard showing security posture, code quality, and team velocity eliminates the need to correlate findings across 3–5 separate tools.
Evaluation criteria that matter:
Criterion | What to Look For | Why It Matters |
Signal Quality | <15% false positive rate with reachability analysis | Developers trust and act on findings |
Feedback Speed | <3 minutes for PR checks, real-time IDE integration | Maintains flow, catches issues pre-merge |
Remediation | One-click auto-fix with context-aware suggestions | Reduces fix time by 60-70% |
Coverage | Unified SAST, DAST, SCA, secrets, IaC in one platform | Eliminates manual correlation across tools |
Integration | Native Git workflow, no separate dashboards | Developers don't context-switch |
The CodeAnt AI Approach: Unified Code Health Across the SDLC
CodeAnt AI redefines vulnerability detection by treating security as part of broader code health. Instead of forcing you to choose between SAST, DAST, SCA, or secrets detection, it delivers all of them through a single AI-native architecture that learns your codebase.
How it Works in Practice…
Real-time PR reviews with context-aware scanning
CodeAnt integrates directly into your pull request workflow, analyzing changes as developers commit code. Unlike traditional SAST tools that rescan entire codebases and flag hundreds of issues, CodeAnt focuses on incremental changes and applies AI-driven context to reduce false positives by 80%.
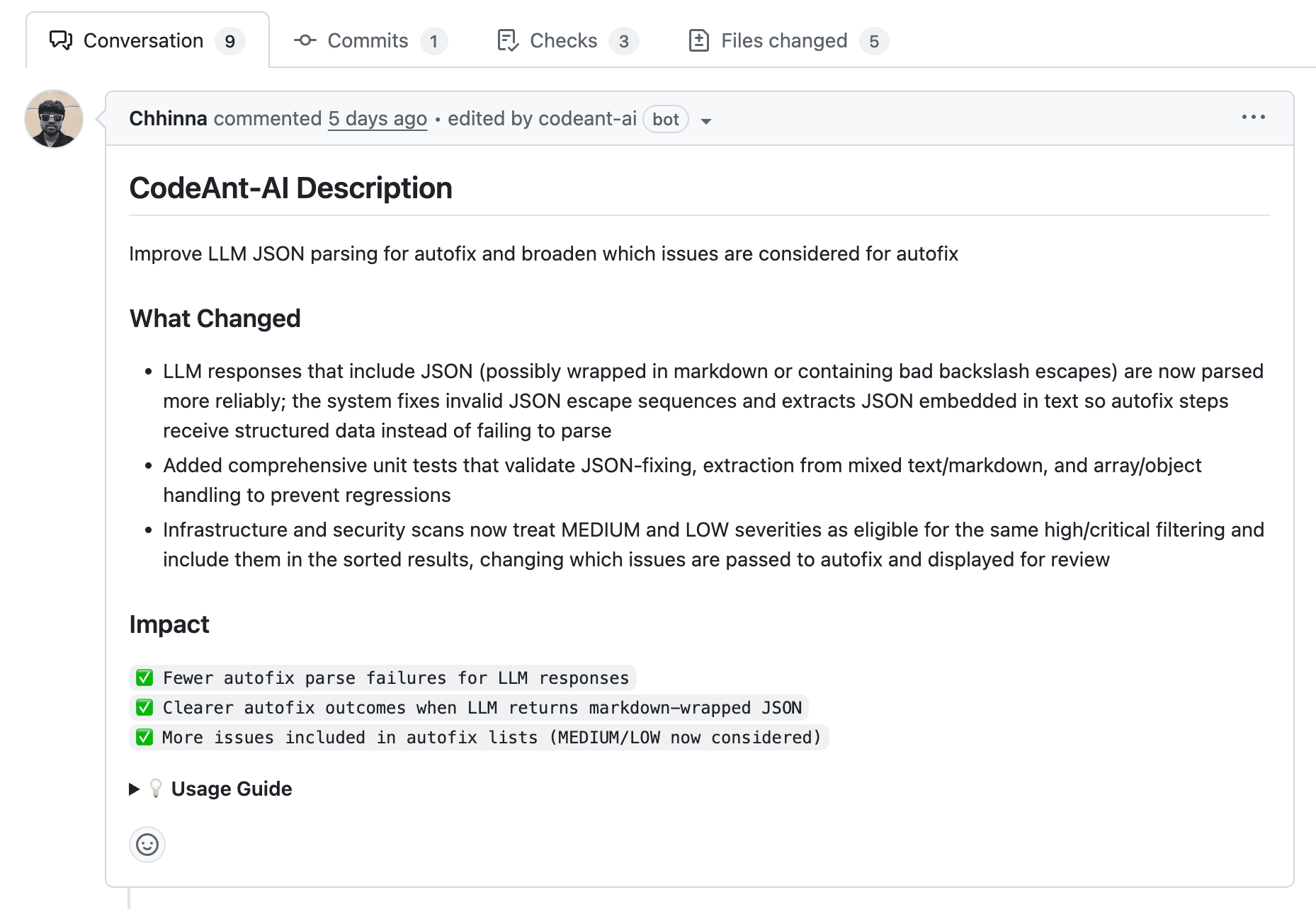
Risk Intelligence Graph for prioritization
CodeAnt correlates findings across static analysis, dependency vulnerabilities, secrets exposure, and runtime behavior. Instead of treating each issue in isolation, it maps exploit paths and shows you which vulnerabilities are actually reachable in production.
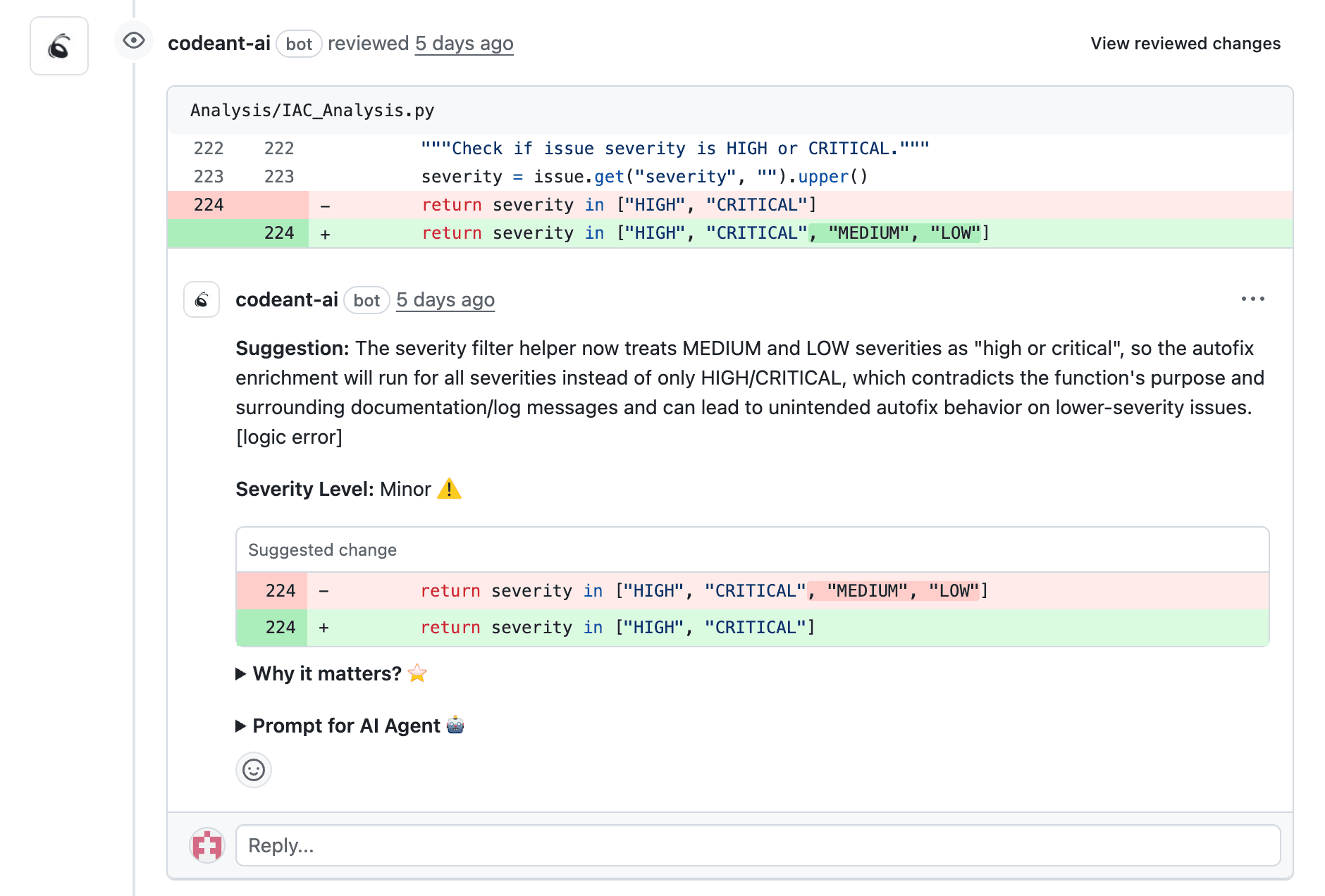
Auto-fix suggestions that developers trust
When CodeAnt flags a vulnerability, it generates a context-aware fix based on your codebase patterns. Developers can apply fixes with one click, eliminating the research overhead that slows remediation.
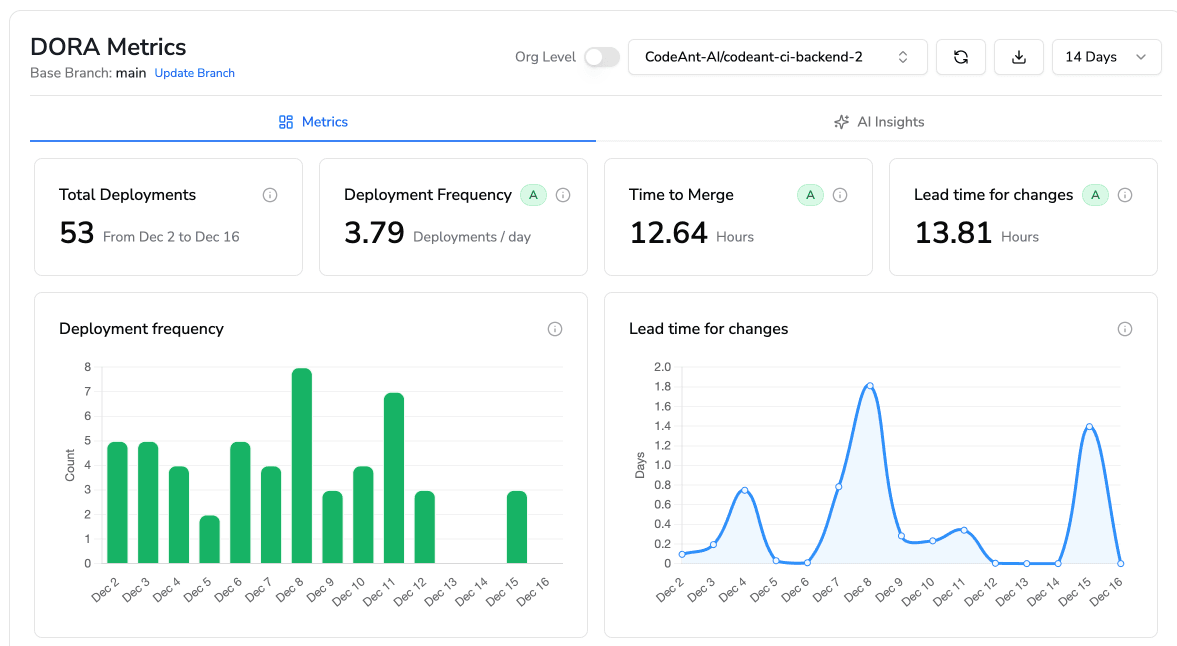
Engineering metrics that connect security to velocity
CodeAnt tracks DORA metrics (deployment frequency, lead time, change failure rate) alongside security posture. This unified view helps engineering leaders understand whether security practices are accelerating or slowing delivery.
Quantifiable Impact
Teams using CodeAnt typically see:
60% faster PR reviews: Real-time feedback eliminates wait for CI scans
80% reduction in false positives: AI-driven context filters noise
$200K+ annual savings for 100-dev teams: Consolidating 3–5 tools
67% fewer post-merge security fixes: Catching issues before merge
Vendor Comparison: How CodeAnt Stacks Up
Capability | CodeAnt AI | GitHub Advanced Security | Snyk | SonarQube | Checkmarx |
Unified SAST + DAST + SCA | ✅ Single platform | ⚠️ SAST + SCA only | ⚠️ Limited SAST | ⚠️ Quality-focused | ❌ Requires add-ons |
AI-powered context | ✅ Learns codebase patterns | ❌ Rule-based | ⚠️ Pattern matching | ❌ Rule-based | ❌ Rule-based |
False positive rate | <20% | 40-60% | 30-40% (SCA), higher (SAST) | 70-80% | 70-80% |
Auto-fix suggestions | ✅ One-click remediation | ⚠️ Copilot (separate license) | ⚠️ Dependency upgrades only | ❌ Manual fixes | ❌ Manual fixes |
Real-time PR feedback | ✅ <2 min | ✅ PR checks | ✅ PR checks | ⚠️ 10-30 min | ⚠️ 20-45 min |
DORA metrics integration | ✅ Security + velocity unified | ⚠️ Basic via Insights | ❌ Security-only | ⚠️ Quality metrics | ❌ Security-only |
Pricing transparency | ✅ $150/10 devs/month | ✅ $21/dev/month | ⚠️ Complex usage-based | ✅ Open-source option | ❌ Enterprise quotes only |
When CodeAnt Wins for Modern Teams
vs. GitHub Advanced Security: GHAS offers tight GitHub integration but requires separate tools for DAST and lacks engineering visibility. CodeAnt provides complete SDLC coverage with unified code health metrics.
vs. Snyk: Snyk leads in SCA but its SAST lags behind dedicated static analysis tools. CodeAnt matches SCA depth while delivering mature SAST, secrets detection, and cross-domain correlation Snyk can't provide.
vs. SonarQube: SonarQube focuses on code quality with security as secondary. CodeAnt inverts this, security-first scanning with auto-fix and compliance automation, plus quality analysis that SonarQube delivers.
vs. Checkmarx: Checkmarx offers mature SAST but forces teams into add-on licensing for SCA, secrets, and IaC. CodeAnt delivers all natively with AI context that rule-based engines can't match, eliminating the 40+ hour configuration burden.
Real-World Impact: What Changes in Production
Fintech: Securing AI-Generated Code at Scale
A 300-developer fintech platform adopted SonarQube but their security stack couldn't assess AI-generated code for context-specific vulnerabilities.
Results after implementing CodeAnt AI:
67% reduction in post-merge security fixes
8.2 hours/week saved in security team triage
PR cycle time decreased from 4.3 hours to 1.7 hours
Zero critical vulnerabilities shipped to production in 90 days
Read the full case study here.
Getting Started: A Practical 2-Week Plan
Week 1: Foundation and Baseline
Day 1–2: Connect and Scan
Connect your Git provider (GitHub, GitLab, Bitbucket) to CodeAnt AI
Baseline scan completes in 15–30 minutes, surfacing existing vulnerabilities
Note your current vulnerability count and false positive rate for comparison
Day 3–4: Configure PR Review Checks
Enable automated PR reviews on 2–3 pilot repositories
Set blocking thresholds based on risk tolerance (start permissive, tighten over time)
Developers see real-time feedback in PR comments within seconds
Day 5: Define Severity Levels and SLOs
Severity | Definition | Remediation SLO | Auto-Fix |
Critical | Exploitable vulnerabilities, exposed secrets | 24 hours | Yes |
High | Reachable security flaws, compliance violations | 7 days | Yes |
Medium | Quality issues, potential risks | 30 days | Optional |
Low | Code smells, minor improvements | Backlog | No |
Week 2: Integration and Automation
Day 6–7: Enable Auto-Fix Policies
Configure auto-fix for SQL injection, XSS, hardcoded secrets, dependency updates
Start conservative, approve fixes manually, then enable auto-merge for trusted patterns
Outcome: 40–60% of security findings resolve without developer intervention
Day 8: Integrate Issue Tracking
Connect CodeAnt to Jira or Linear for automated ticket creation
Map severity levels to your team's priority system
Security work enters sprint planning automatically
Day 9–10: Set Up Compliance Dashboards
Enable compliance frameworks (SOC2, PCI-DSS, HIPAA)
Configure continuous tracking and automated evidence collection
Reduce audit prep time from weeks to days
POC Success Checklist
Developer adoption: 80%+ of PRs reviewed with <5% false positive complaints
Speed improvement: PR review time reduced 40–60%
Security wins: Critical vulnerabilities blocked pre-merge
Tool consolidation: At least one legacy security tool retired
Stakeholder buy-in: Engineering and security leadership see measurable ROI
The Bottom Line
The best vulnerability detection vendor doesn't force you to choose between static and dynamic approaches, it unifies them into a single, context-aware platform that eliminates tool sprawl while accelerating delivery.
Choose CodeAnt AI when you:
Manage 100+ developers across polyglot codebases
Deploy daily and need security feedback in minutes, not hours
Want to consolidate 3+ security tools into one platform
Use AI coding assistants and need to secure generated code
Require compliance automation without manual evidence collection
Your evaluation plan:
Week 1: Connect repositories, run baseline scans, configure PR reviews
Week 2: Enable auto-fix, integrate issue tracking, validate compliance dashboards
Decision point: Calculate ROI based on reduced tool spend, faster reviews, and measurable risk reduction
CodeAnt AI delivers superior detection accuracy, faster developer feedback, and unified engineering visibility in a platform designed for how modern teams actually ship software. Teams using CodeAnt retire an average of 2.4 security tools in their first 90 days while reducing false positives by 80% and accelerating PR reviews by 60%.
Start your 14-day free trial (no credit card required) orbook a 1:1 with our experts to see how unified code health eliminates tool sprawl in your next sprint.














