Your security scanner just flagged 847 vulnerabilities across your codebase. Your architecture diagram looks like a subway map designed by someone who hates commuters. And your team is supposed to fix all of this before the next release.
Here's the problem: treating every line of code with equal scrutiny doesn't make your application safer, it just makes your engineers slower. This guide covers how to identify high-risk code paths, why they deserve disproportionate attention over full-system visualization, and the practical steps to implement risk-focused analysis in your workflow.
What Are High-Risk Code Paths
Focusing on high-risk code paths beats full-system visualization because it directs limited resources toward the code most likely to cause real problems. Full-system visualization, think UML diagrams, dependency graphs, architecture maps, gives you a bird's-eye view of your codebase. But that view often creates information overload without telling you where to actually focus.
High-risk code paths are the sections of your codebase most likely to contain bugs, security vulnerabilities, or trigger system failures. You'll typically find them in predictable places:
Sensitive data handlers: Functions that process authentication, payments, or personally identifiable information (PII)
Complex branching logic: Code with deep nesting or many conditional paths
Frequently modified modules: Areas with high code churn across multiple pull requests
External integration points: API calls, third-party dependencies, and service boundaries
When you know where risk concentrates, you can review that code more carefully and catch issues before they reach production.
Why Full-System Code Visualization Falls Short at Scale
Code visualization tools have their place. They help teams understand how modules connect and how data flows through a system. However, as codebases grow, visualization alone stops being useful and starts becoming noise.
Information Overload Obscures Critical Issues
Visualizing every module, class, and dependency buries the dangerous code paths in clutter. When everything looks equally important, nothing stands out. Developers end up parsing irrelevant information instead of focusing on what actually matters.
Static Diagrams Miss Runtime and Dependency Risks
Traditional visualization shows structure, not behavior. A diagram might show that Module A calls Module B, but it won't reveal that Module B handles unvalidated user input. Runtime vulnerabilities, dynamic dependencies, and execution flow risks don't appear in static architecture diagrams.
Cognitive Load Slows Developer Productivity
Full-system diagrams overwhelm developers during code reviews. Mental fatigue increases, and pull request approvals slow down. Reviewers start skimming instead of scrutinizing, which defeats the purpose of the review.
Equal Treatment of All Code Wastes Engineering Resources
Treating a low-risk utility function the same as an authentication module misallocates review effort. Your team's time is finite. Spending it equally across all code means under-investing in the areas that matter most.
Security Benefits of Focusing on High-Risk Code Paths
Risk-focused analysis strengthens your security posture by prioritizing depth over breadth. Instead of spreading attention thin across the entire codebase, you concentrate on the code most likely to be exploited.
Faster Vulnerability Prioritization
Identifying high-risk paths lets security teams address critical vulnerabilities first. Rather than reviewing findings scattered across hundreds of files, you focus on the code that handles sensitive operations.
More Accurate Threat Modeling
Focusing on risky code paths improves threat modeling accuracy. You're concentrating on attack surfaces that matter, not theoretical risks in rarely-executed code.
Clearer Blast Radius and Impact Analysis
Blast radius refers to the scope of damage if code fails or gets exploited. Risk-focused analysis clarifies potential downstream impact, helping you understand what breaks when something goes wrong.
Better Dependency and Supply Chain Risk Visibility
Risk-based approaches expose vulnerable third-party dependencies within critical code paths. You catch supply chain risks where they actually affect your application, not buried in a dependency tree visualization.
What Makes a Code Path High Risk
Engineering teams identify risky code using a combination of signals. No single metric tells the whole story, but together they paint a clear picture.
Risk Factor | What It Indicates | Why It Matters |
Cyclomatic complexity | Branching density and test difficulty | More branches mean more potential failure points |
Change frequency | Code churn and instability | Frequently changed code introduces regressions |
Dependency count | Coupling and external exposure | More dependencies increase attack surface |
Data sensitivity | Handles PII, credentials, or payments | Higher regulatory and security implications |
Bug history | Past incident patterns | Historical issues predict future failures |
Cyclomatic Complexity and Nesting Depth
Cyclomatic complexity measures the number of independent paths through code. A function with a complexity score of 30 has 30 possible execution paths. Testing all of them becomes impractical, and bugs hide in the untested branches.
Change Frequency and Code Churn
Code modified frequently across multiple pull requests often contains latent bugs or incomplete refactors. High churn correlates with higher defect rates. If a module has been touched in 50 PRs over the last quarter, it deserves closer attention.
Dependency Count and Tight Coupling
Tightly coupled code with many dependencies amplifies risk. A single failure cascades through connected modules. The more dependencies a critical path has, the larger its attack surface.
Security Surface Area and Data Sensitivity
Code handling authentication, encryption, or sensitive user data requires higher scrutiny regardless of complexity. Even simple code becomes high-risk when it touches credentials or payment information.
Historical Bug Density and Incident Patterns
Past incident data reveals code areas prone to recurring issues. If a module has caused production incidents before, it deserves ongoing attention. History tends to repeat itself.
How to Identify High-Risk Code Paths in Your Codebase
Here's a practical process for finding where risk concentrates in your codebase.
1. Analyze Complexity Metrics Across Modules
Use static analysis to surface modules with high cyclomatic complexity, deep nesting, or excessive line counts. Most static analysis tools generate complexity metrics automatically.
2. Map Dependency Relationships and Coupling Patterns
Dependency graphs help identify tightly coupled components and single points of failure. Look for modules that many other modules depend on. Those are your critical paths.
3. Review Change History and Incident Data
Git history and incident tracking systems reveal hotspots with frequent changes or past bugs. A module that's been modified in dozens of PRs over the last quarter deserves closer attention.
4. Integrate Risk Analysis Into Pull Request Reviews
Embed risk context directly into code review workflows so reviewers see high-risk flags before approving merges. CodeAnt AI surfaces risk indicators automatically during PR review, including sequence diagrams that capture the core runtime flow introduced by each change.
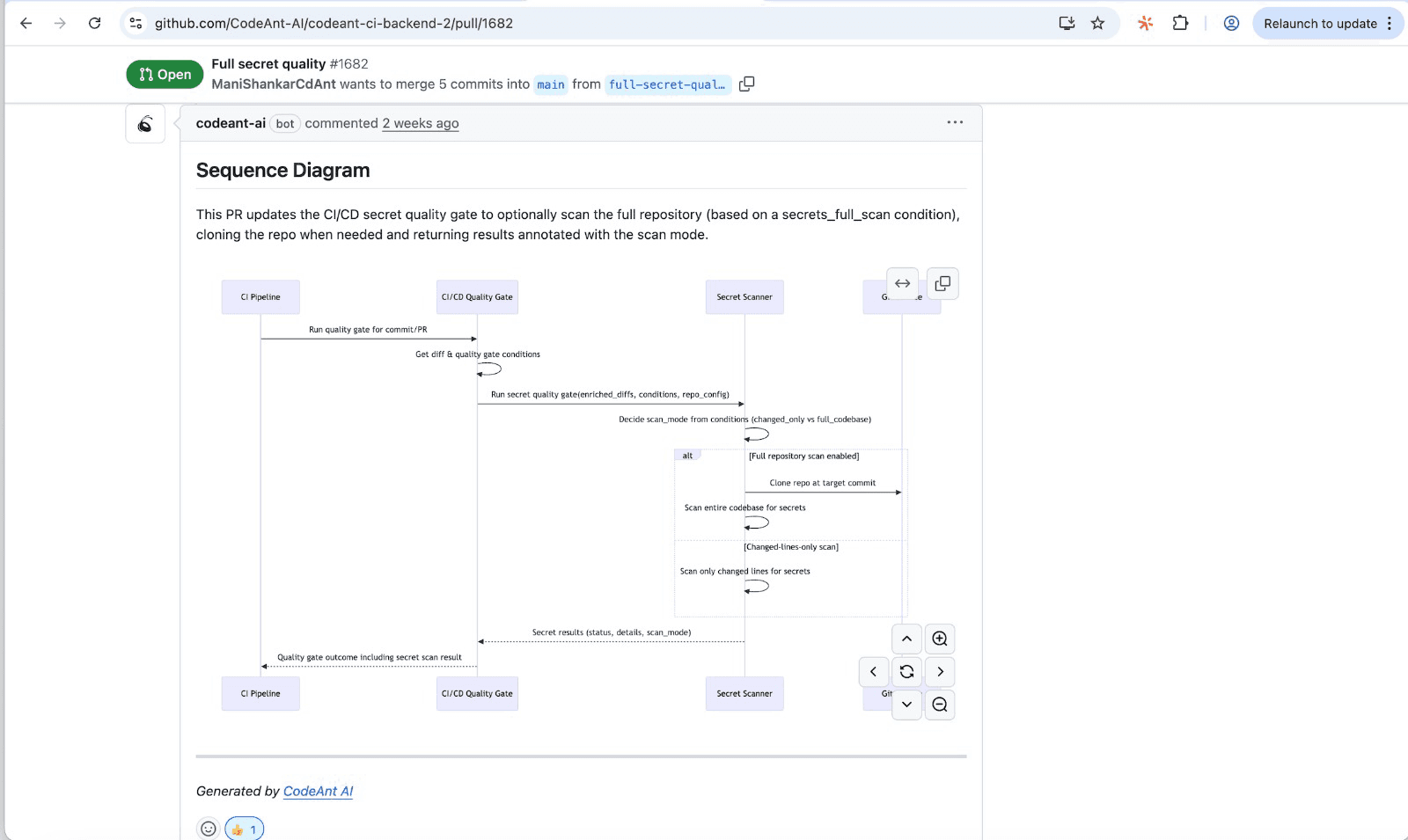
5. Automate Continuous Risk Monitoring in CI/CD
Automated pipelines can continuously scan for risk indicators and block merges when critical thresholds are exceeded. This prevents high-risk code from slipping through during busy periods.
How Risk-Focused Analysis Outperforms Full-System Visualization
The difference between risk-focused analysis and full-system visualization comes down to signal versus noise.
Faster Detection of Critical Issues
Narrowing focus accelerates time-to-detection for security vulnerabilities and bugs. You're not searching through an entire system diagram. You're looking exactly where problems are most likely to occur.
More Accurate Risk Prioritization
Risk-based approaches align remediation effort with actual business impact. A vulnerability in your payment processing code matters more than one in an internal admin tool.
Better Resource Efficiency and ROI
Engineering teams spend less time on low-value code and more on what matters. This translates directly to faster releases and fewer production incidents.
Seamless Integration With Code Review Workflows
Risk analysis embeds into existing pull request workflows. Unlike full-system visualization tools that live outside the development loop, risk-focused tools meet developers where they already work.
Tip: For every PR, CodeAnt AI generates a sequence diagram capturing the core runtime flow, showing which modules interact, in what order, and where key decision points happen. Reviewers get a one-shot, high-signal glance at what the PR actually does.

Essential Features for Risk-Focused Code Analysis Tools
When evaluating tools for risk-based code analysis, look for capabilities that surface risk automatically and integrate into your existing workflow.
AI-Driven Risk Identification
AI models detect patterns humans miss. They identify risky code paths based on learned indicators across thousands of codebases, not just static rules.
Automated Pull Request Review With Risk Context
Tools flag high-risk changes directly in PRs with contextual explanations. Reviewers immediately understand why a change deserves extra scrutiny.
Dependency Scanning and Vulnerability Detection
Built-in scanning for vulnerable dependencies, secrets exposure, and misconfigurations within high-risk paths catches issues before they reach production.
Configurable Quality Gates and Policy Enforcement
Teams can define organization-specific risk thresholds and block merges that violate standards. This prevents high-risk code from bypassing review.
Unified Dashboards for Code Health Metrics
Centralized visibility into complexity, coverage, duplication, and risk trends across repositories helps engineering leaders track progress over time.
Metrics to Track When Prioritizing High-Risk Code Paths
Tracking the right metrics helps you measure whether your risk-focused approach is working.
Mean Time to Remediate Critical Findings
MTTR for security findings measures how quickly your team fixes vulnerabilities. Faster remediation in high-risk areas reduces exposure windows.
Vulnerability Density in High-Risk Modules
Track vulnerability counts per module to monitor whether risk concentration is decreasing over time. A downward trend indicates your prioritization is working.
Change Failure Rate in Critical Paths
Track failed deployments or rollbacks originating from high-risk code areas. This DORA metric reveals whether your high-risk code is actually more stable.
Code Coverage for High-Risk Areas
Prioritize test coverage in risky modules over achieving uniform coverage across the entire codebase. 90% coverage in your authentication module matters more than 90% coverage overall.
Technical Debt Concentration Ratio
Measure how much technical debt accumulates in high-risk versus low-risk code paths. Debt in critical paths compounds faster and causes more damage.
Best Practices for Implementing Risk-Based Code Analysis
1. Start With Your Most Critical Services and Repositories
Pilot risk-focused analysis on revenue-critical or security-sensitive codebases first. Prove value before rolling out organization-wide.
2. Define Risk Thresholds Aligned With Your Organization
Risk criteria reflect your industry, compliance requirements, and risk tolerance. A fintech company has different thresholds than a gaming studio.
3. Embed Risk Analysis Into Every Pull Request
Make risk visibility a default part of code review, not an afterthought. CodeAnt AI integrates risk context directly into PR workflows, including visual sequence diagrams of runtime flow.
4. Communicate Risk Prioritization to Non-Technical Stakeholders
Translate risk metrics into business impact for leadership and compliance teams. "This module handles 80% of our payment transactions" resonates more than "cyclomatic complexity of 47."
5. Review and Refine Risk Criteria Based on Outcomes
Iterate on risk definitions as you learn which indicators correlate with actual incidents. Your risk model improves over time.
How to Build a Risk-First Code Health Strategy
Risk-focused analysis isn't about ignoring the rest of your codebase. It's about directing attention where it matters most. Full-system visualization has its place, but it can't replace targeted, risk-aware review.
The most effective teams combine baseline static analysis across their entire codebase with deep, concentrated review on critical paths. They use AI-driven tools to surface risk automatically, embed risk context into every pull request, and track metrics that measure actual outcomes.
CodeAnt AI unifies risk identification, automated code review, and security scanning into a single view of code health. Every PR includes a sequence diagram showing the core runtime flow, so reviewers understand what changed, where it propagates, and what could break.
Ready to focus your engineering effort where it matters most?Check out our self-hosted version of code health platform here,
Your security scanner just flagged 847 vulnerabilities across your codebase. Your architecture diagram looks like a subway map designed by someone who hates commuters. And your team is supposed to fix all of this before the next release.
Here's the problem: treating every line of code with equal scrutiny doesn't make your application safer, it just makes your engineers slower. This guide covers how to identify high-risk code paths, why they deserve disproportionate attention over full-system visualization, and the practical steps to implement risk-focused analysis in your workflow.
What Are High-Risk Code Paths
Focusing on high-risk code paths beats full-system visualization because it directs limited resources toward the code most likely to cause real problems. Full-system visualization, think UML diagrams, dependency graphs, architecture maps, gives you a bird's-eye view of your codebase. But that view often creates information overload without telling you where to actually focus.
High-risk code paths are the sections of your codebase most likely to contain bugs, security vulnerabilities, or trigger system failures. You'll typically find them in predictable places:
Sensitive data handlers: Functions that process authentication, payments, or personally identifiable information (PII)
Complex branching logic: Code with deep nesting or many conditional paths
Frequently modified modules: Areas with high code churn across multiple pull requests
External integration points: API calls, third-party dependencies, and service boundaries
When you know where risk concentrates, you can review that code more carefully and catch issues before they reach production.
Why Full-System Code Visualization Falls Short at Scale
Code visualization tools have their place. They help teams understand how modules connect and how data flows through a system. However, as codebases grow, visualization alone stops being useful and starts becoming noise.
Information Overload Obscures Critical Issues
Visualizing every module, class, and dependency buries the dangerous code paths in clutter. When everything looks equally important, nothing stands out. Developers end up parsing irrelevant information instead of focusing on what actually matters.
Static Diagrams Miss Runtime and Dependency Risks
Traditional visualization shows structure, not behavior. A diagram might show that Module A calls Module B, but it won't reveal that Module B handles unvalidated user input. Runtime vulnerabilities, dynamic dependencies, and execution flow risks don't appear in static architecture diagrams.
Cognitive Load Slows Developer Productivity
Full-system diagrams overwhelm developers during code reviews. Mental fatigue increases, and pull request approvals slow down. Reviewers start skimming instead of scrutinizing, which defeats the purpose of the review.
Equal Treatment of All Code Wastes Engineering Resources
Treating a low-risk utility function the same as an authentication module misallocates review effort. Your team's time is finite. Spending it equally across all code means under-investing in the areas that matter most.
Security Benefits of Focusing on High-Risk Code Paths
Risk-focused analysis strengthens your security posture by prioritizing depth over breadth. Instead of spreading attention thin across the entire codebase, you concentrate on the code most likely to be exploited.
Faster Vulnerability Prioritization
Identifying high-risk paths lets security teams address critical vulnerabilities first. Rather than reviewing findings scattered across hundreds of files, you focus on the code that handles sensitive operations.
More Accurate Threat Modeling
Focusing on risky code paths improves threat modeling accuracy. You're concentrating on attack surfaces that matter, not theoretical risks in rarely-executed code.
Clearer Blast Radius and Impact Analysis
Blast radius refers to the scope of damage if code fails or gets exploited. Risk-focused analysis clarifies potential downstream impact, helping you understand what breaks when something goes wrong.
Better Dependency and Supply Chain Risk Visibility
Risk-based approaches expose vulnerable third-party dependencies within critical code paths. You catch supply chain risks where they actually affect your application, not buried in a dependency tree visualization.
What Makes a Code Path High Risk
Engineering teams identify risky code using a combination of signals. No single metric tells the whole story, but together they paint a clear picture.
Risk Factor | What It Indicates | Why It Matters |
Cyclomatic complexity | Branching density and test difficulty | More branches mean more potential failure points |
Change frequency | Code churn and instability | Frequently changed code introduces regressions |
Dependency count | Coupling and external exposure | More dependencies increase attack surface |
Data sensitivity | Handles PII, credentials, or payments | Higher regulatory and security implications |
Bug history | Past incident patterns | Historical issues predict future failures |
Cyclomatic Complexity and Nesting Depth
Cyclomatic complexity measures the number of independent paths through code. A function with a complexity score of 30 has 30 possible execution paths. Testing all of them becomes impractical, and bugs hide in the untested branches.
Change Frequency and Code Churn
Code modified frequently across multiple pull requests often contains latent bugs or incomplete refactors. High churn correlates with higher defect rates. If a module has been touched in 50 PRs over the last quarter, it deserves closer attention.
Dependency Count and Tight Coupling
Tightly coupled code with many dependencies amplifies risk. A single failure cascades through connected modules. The more dependencies a critical path has, the larger its attack surface.
Security Surface Area and Data Sensitivity
Code handling authentication, encryption, or sensitive user data requires higher scrutiny regardless of complexity. Even simple code becomes high-risk when it touches credentials or payment information.
Historical Bug Density and Incident Patterns
Past incident data reveals code areas prone to recurring issues. If a module has caused production incidents before, it deserves ongoing attention. History tends to repeat itself.
How to Identify High-Risk Code Paths in Your Codebase
Here's a practical process for finding where risk concentrates in your codebase.
1. Analyze Complexity Metrics Across Modules
Use static analysis to surface modules with high cyclomatic complexity, deep nesting, or excessive line counts. Most static analysis tools generate complexity metrics automatically.
2. Map Dependency Relationships and Coupling Patterns
Dependency graphs help identify tightly coupled components and single points of failure. Look for modules that many other modules depend on. Those are your critical paths.
3. Review Change History and Incident Data
Git history and incident tracking systems reveal hotspots with frequent changes or past bugs. A module that's been modified in dozens of PRs over the last quarter deserves closer attention.
4. Integrate Risk Analysis Into Pull Request Reviews
Embed risk context directly into code review workflows so reviewers see high-risk flags before approving merges. CodeAnt AI surfaces risk indicators automatically during PR review, including sequence diagrams that capture the core runtime flow introduced by each change.

5. Automate Continuous Risk Monitoring in CI/CD
Automated pipelines can continuously scan for risk indicators and block merges when critical thresholds are exceeded. This prevents high-risk code from slipping through during busy periods.
How Risk-Focused Analysis Outperforms Full-System Visualization
The difference between risk-focused analysis and full-system visualization comes down to signal versus noise.
Faster Detection of Critical Issues
Narrowing focus accelerates time-to-detection for security vulnerabilities and bugs. You're not searching through an entire system diagram. You're looking exactly where problems are most likely to occur.
More Accurate Risk Prioritization
Risk-based approaches align remediation effort with actual business impact. A vulnerability in your payment processing code matters more than one in an internal admin tool.
Better Resource Efficiency and ROI
Engineering teams spend less time on low-value code and more on what matters. This translates directly to faster releases and fewer production incidents.
Seamless Integration With Code Review Workflows
Risk analysis embeds into existing pull request workflows. Unlike full-system visualization tools that live outside the development loop, risk-focused tools meet developers where they already work.
Tip: For every PR, CodeAnt AI generates a sequence diagram capturing the core runtime flow, showing which modules interact, in what order, and where key decision points happen. Reviewers get a one-shot, high-signal glance at what the PR actually does.

Essential Features for Risk-Focused Code Analysis Tools
When evaluating tools for risk-based code analysis, look for capabilities that surface risk automatically and integrate into your existing workflow.
AI-Driven Risk Identification
AI models detect patterns humans miss. They identify risky code paths based on learned indicators across thousands of codebases, not just static rules.
Automated Pull Request Review With Risk Context
Tools flag high-risk changes directly in PRs with contextual explanations. Reviewers immediately understand why a change deserves extra scrutiny.
Dependency Scanning and Vulnerability Detection
Built-in scanning for vulnerable dependencies, secrets exposure, and misconfigurations within high-risk paths catches issues before they reach production.
Configurable Quality Gates and Policy Enforcement
Teams can define organization-specific risk thresholds and block merges that violate standards. This prevents high-risk code from bypassing review.
Unified Dashboards for Code Health Metrics
Centralized visibility into complexity, coverage, duplication, and risk trends across repositories helps engineering leaders track progress over time.
Metrics to Track When Prioritizing High-Risk Code Paths
Tracking the right metrics helps you measure whether your risk-focused approach is working.
Mean Time to Remediate Critical Findings
MTTR for security findings measures how quickly your team fixes vulnerabilities. Faster remediation in high-risk areas reduces exposure windows.
Vulnerability Density in High-Risk Modules
Track vulnerability counts per module to monitor whether risk concentration is decreasing over time. A downward trend indicates your prioritization is working.
Change Failure Rate in Critical Paths
Track failed deployments or rollbacks originating from high-risk code areas. This DORA metric reveals whether your high-risk code is actually more stable.
Code Coverage for High-Risk Areas
Prioritize test coverage in risky modules over achieving uniform coverage across the entire codebase. 90% coverage in your authentication module matters more than 90% coverage overall.
Technical Debt Concentration Ratio
Measure how much technical debt accumulates in high-risk versus low-risk code paths. Debt in critical paths compounds faster and causes more damage.
Best Practices for Implementing Risk-Based Code Analysis
1. Start With Your Most Critical Services and Repositories
Pilot risk-focused analysis on revenue-critical or security-sensitive codebases first. Prove value before rolling out organization-wide.
2. Define Risk Thresholds Aligned With Your Organization
Risk criteria reflect your industry, compliance requirements, and risk tolerance. A fintech company has different thresholds than a gaming studio.
3. Embed Risk Analysis Into Every Pull Request
Make risk visibility a default part of code review, not an afterthought. CodeAnt AI integrates risk context directly into PR workflows, including visual sequence diagrams of runtime flow.
4. Communicate Risk Prioritization to Non-Technical Stakeholders
Translate risk metrics into business impact for leadership and compliance teams. "This module handles 80% of our payment transactions" resonates more than "cyclomatic complexity of 47."
5. Review and Refine Risk Criteria Based on Outcomes
Iterate on risk definitions as you learn which indicators correlate with actual incidents. Your risk model improves over time.
How to Build a Risk-First Code Health Strategy
Risk-focused analysis isn't about ignoring the rest of your codebase. It's about directing attention where it matters most. Full-system visualization has its place, but it can't replace targeted, risk-aware review.
The most effective teams combine baseline static analysis across their entire codebase with deep, concentrated review on critical paths. They use AI-driven tools to surface risk automatically, embed risk context into every pull request, and track metrics that measure actual outcomes.
CodeAnt AI unifies risk identification, automated code review, and security scanning into a single view of code health. Every PR includes a sequence diagram showing the core runtime flow, so reviewers understand what changed, where it propagates, and what could break.
Ready to focus your engineering effort where it matters most?Check out our self-hosted version of code health platform here,
FAQs
How do you prevent blind spots when focusing only on high-risk paths?
Can low-risk code still contain critical security vulnerabilities?
What codebase size benefits most from risk-based code analysis?
How long does it take to see ROI from prioritizing high-risk code paths?
How do you reduce false positives when identifying high-risk code?
Table of Contents
Start Your 14-Day Free Trial
AI code reviews, security, and quality trusted by modern engineering teams. No credit card required!
Share blog:















