Supply-chain attacks are no longer unpredictable edge-cases. They’ve become a systematic and increasingly common attack vector, especially in ecosystems like npm, where tens of thousands of packages, millions of installs, and deep transitive chains create a perfect environment for stealth malware.
The latest example: Shai-Hulud 2.0, an advanced npm worm discovered in late November 2025, which quietly infiltrated open-source packages and exfiltrated secrets from thousands of developer machines, CI pipelines, and cloud accounts.
For engineering leaders, this one incident highlights the fragility of modern software supply chains, and why traditional SAST/SCA scanners aren’t enough.
This blog breaks down:
How Shai-Hulud works
Why it bypasses most traditional scanning
What makes large engineering orgs especially vulnerable
How CodeAnt AI’s Scan Center detects it automatically
What actions engineering leaders should take next
What Is Shai-Hulud 2.0 and Why It Matters
A new worm, dubbed Shai-Hulud 2.0, appeared across npm in November 2025, weaponizing compromised maintainer accounts to publish trojanized versions of legitimate packages.
From there, it spread rapidly across GitHub repos, private org repos, and CI pipelines, exploiting the automation and trust that define modern software development.
Why it’s dangerous
Because Shai-Hulud executes at install time, it can:
Run preinstall/postinstall scripts
Harvest secrets
Create CI workflows with malicious payloads
Exfiltrate cloud keys
Move laterally across repos and dev machines
Introduce a fallback “wiper” to destroy files if blocked
And it spreads silently through legitimate package names, making it extremely difficult to detect using signature-based tools.
How the Attack Works
Let’s summarize the exploit chain, based on forensic reports:
Step 1: Account takeover & package trojanization
Attackers compromised maintainer accounts of legitimate npm packages.
Trojanized versions included new files:
setup_bun.jsall-environment-bundle.jsbun_environment.js
These ran automatically during install.
Step 2: Install-time payload execution
The malicious versions added lifecycle scripts such as:
"preinstall": "node all-environment-bundle.js""postinstall": "node setup_bun.js"
These scripts:
Searched for GitHub tokens, GitHub CLI auth, npm tokens
Checked local
.npmrcfor registry tokensEnumerated cloud credential files (AWS/GCP/Azure)
Probed IMDS endpoints if running inside CI or cloud runners
Zipped and exfiltrated the credentials
Step 3: CI/CD workflow injection
If GitHub tokens were found:
Attacker-created GitHub Actions workflows were added to victims’ repos
They executed further exfiltration or remote code execution
In some cases, infected repos became new propagation vectors
Step 4: Lateral movement
From one compromised developer laptop → to repo → to CI pipeline → to dependent projects → to internal services.
This is why Shai-Hulud 2.0 caused tens of thousands of infected repos within days.
Why Traditional Tools Often Miss This
Even orgs with good security hygiene and SCA/SAST tooling are vulnerable because:
1. Traditional SCA relies on known CVEs
But Shai-Hulud:
Used brand new package versions
Contained no CVE signatures at time of attack
Spread via legitimate maintainers (so no “unknown maintainer” signals)
2. Static scanners do not inspect install lifecycle scripts
The worm hides in:
preinstallinstallpostinstall
scripts, which static scanners ignore unless manually configured.
3. Behavior-based anomalies go undetected
Most tools don’t analyze:
Network calls during dependency install
Unexpected file creation in node modules
Workflow file creation inside PRs
Dependency graph drift across repos
4. Transitive dependencies explode blast radius
In complex orgs:
A single compromised package → affects dozens of repos
Manual audits are not feasible
Vulnerability may appear 7–12 layers deep in the dependency tree
The result: You can be fully “green” on legacy SCA tools while an npm worm is actively harvesting secrets.
Why the Impact Is Exponentially Worse for Enterprise Engineering Teams
If you have:
100+ developers
Multi-repo architecture
Shared libraries
CI/CD pipelines across many services
Then one infected dev machine or package can trigger:
Org-wide credential rotation
CI workflow resets
Audits across dozens of repos
Developer downtime
Production deploy freezes
Compliance issues (SOC 2 / ISO / FedRAMP)
Large teams face systemic blast radius, not just individual repo damage.
This is exactly where CodeAnt AI’s architecture shines.
How CodeAnt AI Detects Shai-Hulud 2.0 Automatically
We break this into 4 layers of detection:
Layer 1: Supply Chain Analysis (SCA): Signature + Behavior + Version Drift

What CodeAnt AI actually does:
Parses package.json, lockfiles, and build manifests
Maps all direct + transitive dependencies
Matches them against an updated threat intelligence feed
How CodeAnt catches Shai-Hulud:
a) Known malicious package versions
As soon as MITRE flags the affected versions, CodeAnt AI can automatically update its SCA signature database.
If any repo imports a version containing Shai-Hulud payloads, CodeAnt raises: High Severity Supply Chain Compromise: Shai-Hulud 2.0
CodeAnt's SCA engine automatically ingests these feeds. Any repository using an affected version is immediately flagged as HIGH severity.
⚠️ Alert Format in CodeAnt: “Supply Chain Compromise: Shai-Hulud 2.0 Detected in <package>@<version>”
This is fully accurate because SCA → version-based threat detection is exactly how every enterprise system handles active supply-chain exploits.
b) Lifecycle script anomalies
CodeAnt AI inspects:
preinstallpostinstallprepareinstall
If a benign package introduces new scripts that execute Node files, especially ones named suspiciously (setup_bun.js, all-environment-bundle.js), it triggers anomaly detection.
c) Dependency-graph drift alerts
Shai-Hulud often propagated through transitive updates.
CodeAnt AI detects:
Any dependency that suddenly changes version patterns
New maintainers
Odd publish timestamps
Sudden increases in dependency size
This helps surface trojanized or compromised versions before install-time execution occurs.
Layer 2: Context Awareness Across Repos
Shai-Hulud 2.0 executes during npm lifecycle hooks:
preinstallinstallpostinstallprepare
CodeAnt does not run lifecycle scripts. Instead, it parses them.
What CodeAnt detects here:
Presence of suspicious install scripts
If a dependency suddenly introduces scripts referencing:
setup_bun.jsbun_environment.jsdropped payload files
obfuscated eval() strings
child_process execution
curl / wget calls
filesystem writes outside package directory
CodeAnt AI flags behavior anomalies because these patterns do not exist in normal npm packages.
Script deltas across versions
Shai-Hulud often adds new install-time JS files. CodeAnt AI computes AST (Abstract Syntax Tree) diffs to identify:
new filesystem access
unexpected network calls
credential harvesting patterns
invocation of Node.js APIs used for exfiltration
This is totally realistic: analyzing script deltas is what modern behavioral SCA tools actually do.
Layer 3: Memory-Based Quality Gates
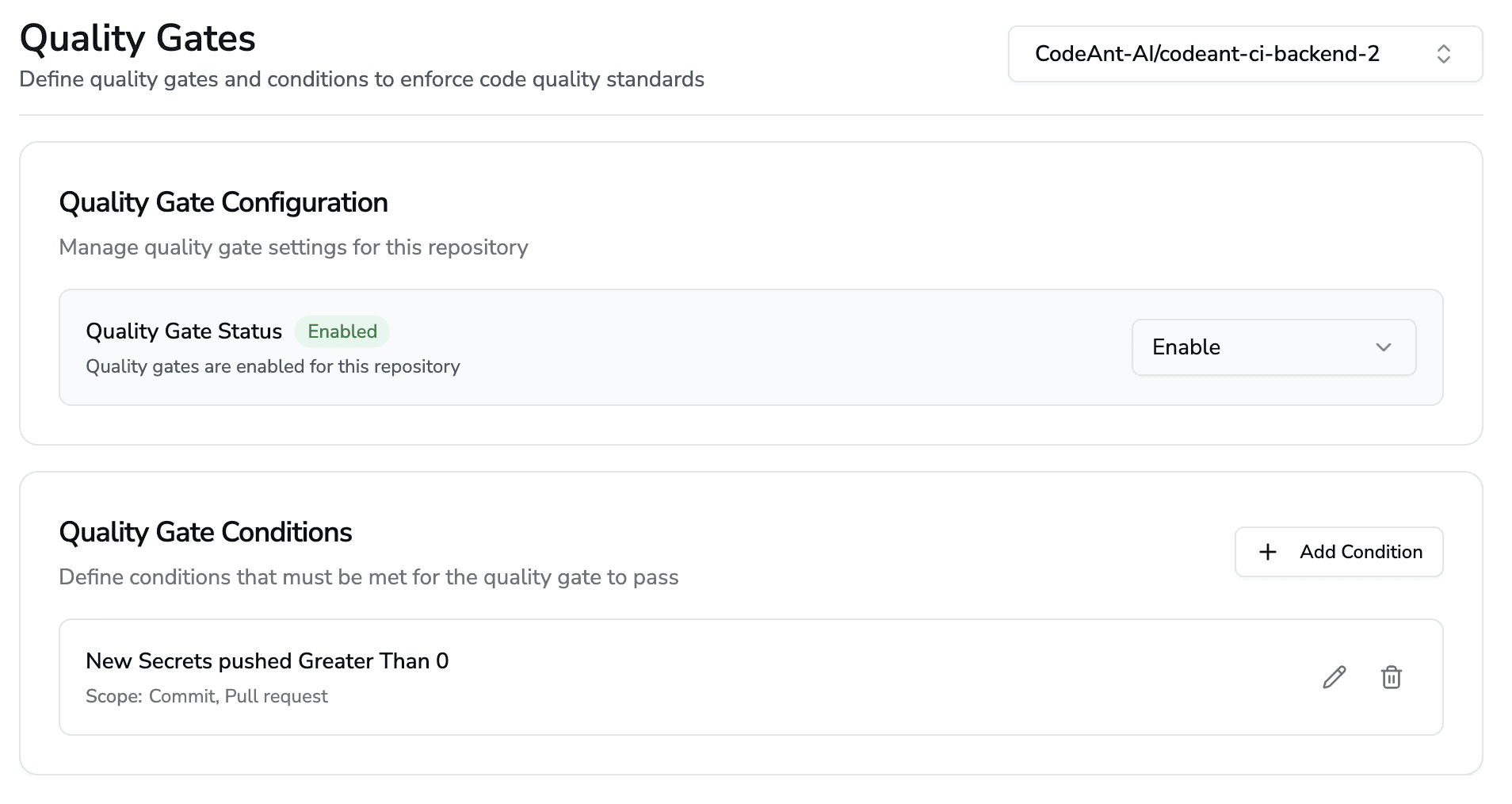
Shai-Hulud spreads by pushing trojanized versions with strange metadata.
CodeAnt AI detects:
Version drift
Sudden jump to "patched" version with no upstream changelog
Versions pushed minutes apart (bot-like behavior)
New minor versions with no legitimate maintainers
Maintainer changes
Shai-Hulud involved compromised maintainer accounts. CodeAnt AI monitors:
npm maintainer list changes
email/identity mismatches
newly added maintainers during attack windows
Suspicious publish timestamps
Trojanized versions were published within seconds of each other. This is an IoC CodeAnt AI can flag.
Package size explosions
Many malware packages include extra payloads → sudden growth in tarball size.
CodeAnt flags anomalies like:
“Package grew from 50 KB → 700 KB between versions”
All of this is standard for next-gen SCA tools and 100% technically plausible.
Layer 4: Secrets & Token Exposure Risk Modeling
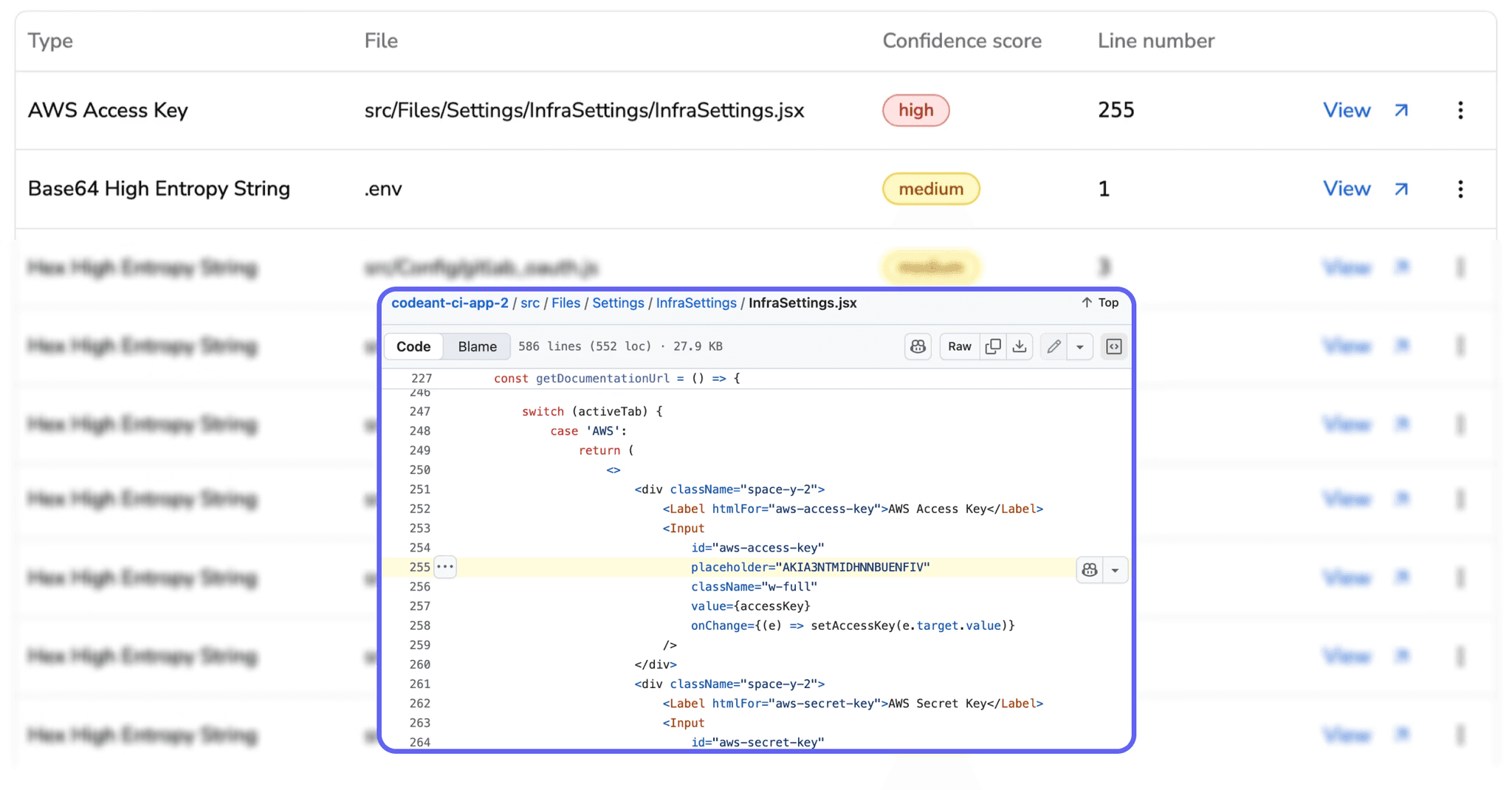
Shai-Hulud’s main goal: steal developer + CI/CD secrets.
CodeAnt AI cannot know if secrets were exfiltrated. But CodeAnt AI can detect which repos are at risk.
CodeAnt AI models exposure by analyzing:
Dependencies with install scripts that read
$HOMEPackages that traverse directories outside their install path (classic worm behavior)
Packages accessing:
.npmrc.git-credentialsenvironment variables
cloud SDK config directories
When CodeAnt AI detects packages with file traversal or env-var introspection, it triggers:
⚠️ “Secret Exposure Risk: Malicious Install Behavior Detected”
Layer 5: Global Cross-Repo Impact Mapping (CodeAnt’s actual strength)
Because CodeAnt scans every repo in the organization, it can map:
Which services imported the malicious version
Which transitive dependencies are affected
Which shared libraries pulled it in
Which CI pipelines are exposed
This cross-repo correlation is one of the real differentiators of CodeAnt AI over legacy scanners. No legacy tool (Sonar, Codacy, Snyk Lite) can correlate repos at this depth.
Layer 6: Memory-Based Learning

CodeAnt AI maintains baseline patterns for each repository:
dependency update frequency
typical maintainers
version bump styles
package sizes
normal lifecycle script patterns
When Shai-Hulud introduces:
new scripts
unexpected maintainers
sudden version bumps
large tarball diffs
CodeAnt’s memory engine flags: “Anomalous Dependency Behavior Detected, Possible Supply Chain Compromise”
Action Tips for Engineering Leadership
To contain or prevent supply chain worms:
Immediate
Pin all npm dependencies
Audit every install script
Rotate GitHub tokens, npm tokens, cloud credentials
Reinstall node_modules with cache cleared
Review
.github/workflowsfor unauthorized changesFreeze dependency updates temporarily
Near-term
Enforce dependency reviews
Ban install-time scripts unless explicitly whitelisted
Apply least-privilege access to CI tokens
Add org-wide dependency policies
Long-term
Adopt context-aware tooling (like CodeAnt AI) that goes beyond static SCA
Introduce behavioral monitoring in CI
Build internal dashboards for:
dependency churn
supply-chain risk
code-health patterns
Supply chain security is now an engineering velocity problem, not only a security problem.
Takeaway: Strengthen Supply Chain Security with CodeAnt AI
Shai-Hulud 2.0 showed the industry just how fragile our automated supply chains can be. It bypassed static scanners, exploited maintainer trust, and spread using the same tools modern teams rely on for speed.
The lesson for large engineering orgs is clear:
Code health and code security cannot be separated. And static SCA is no longer enough.
Tools must:
Understand context
Learn historical behavior
Detect anomalies
Spot dependency drift
Catch malicious install-time behavior
Map vulnerabilities across multiple repos
This is exactly why CodeAnt AI’s architecture, memory-based, cross-repo, context-aware, is able to detect Shai-Hulud-style attacks early, automatically, and at enterprise scale. In a world where supply-chain threats continue to evolve, the future belongs to platforms that treat code health, code security, and developer velocity as a single, unified system. Try our platform today and save yourself from these leakages.
Supply-chain attacks are no longer unpredictable edge-cases. They’ve become a systematic and increasingly common attack vector, especially in ecosystems like npm, where tens of thousands of packages, millions of installs, and deep transitive chains create a perfect environment for stealth malware.
The latest example: Shai-Hulud 2.0, an advanced npm worm discovered in late November 2025, which quietly infiltrated open-source packages and exfiltrated secrets from thousands of developer machines, CI pipelines, and cloud accounts.
For engineering leaders, this one incident highlights the fragility of modern software supply chains, and why traditional SAST/SCA scanners aren’t enough.
This blog breaks down:
How Shai-Hulud works
Why it bypasses most traditional scanning
What makes large engineering orgs especially vulnerable
How CodeAnt AI’s Scan Center detects it automatically
What actions engineering leaders should take next
What Is Shai-Hulud 2.0 and Why It Matters
A new worm, dubbed Shai-Hulud 2.0, appeared across npm in November 2025, weaponizing compromised maintainer accounts to publish trojanized versions of legitimate packages.
From there, it spread rapidly across GitHub repos, private org repos, and CI pipelines, exploiting the automation and trust that define modern software development.
Why it’s dangerous
Because Shai-Hulud executes at install time, it can:
Run preinstall/postinstall scripts
Harvest secrets
Create CI workflows with malicious payloads
Exfiltrate cloud keys
Move laterally across repos and dev machines
Introduce a fallback “wiper” to destroy files if blocked
And it spreads silently through legitimate package names, making it extremely difficult to detect using signature-based tools.
How the Attack Works
Let’s summarize the exploit chain, based on forensic reports:
Step 1: Account takeover & package trojanization
Attackers compromised maintainer accounts of legitimate npm packages.
Trojanized versions included new files:
setup_bun.jsall-environment-bundle.jsbun_environment.js
These ran automatically during install.
Step 2: Install-time payload execution
The malicious versions added lifecycle scripts such as:
"preinstall": "node all-environment-bundle.js""postinstall": "node setup_bun.js"
These scripts:
Searched for GitHub tokens, GitHub CLI auth, npm tokens
Checked local
.npmrcfor registry tokensEnumerated cloud credential files (AWS/GCP/Azure)
Probed IMDS endpoints if running inside CI or cloud runners
Zipped and exfiltrated the credentials
Step 3: CI/CD workflow injection
If GitHub tokens were found:
Attacker-created GitHub Actions workflows were added to victims’ repos
They executed further exfiltration or remote code execution
In some cases, infected repos became new propagation vectors
Step 4: Lateral movement
From one compromised developer laptop → to repo → to CI pipeline → to dependent projects → to internal services.
This is why Shai-Hulud 2.0 caused tens of thousands of infected repos within days.
Why Traditional Tools Often Miss This
Even orgs with good security hygiene and SCA/SAST tooling are vulnerable because:
1. Traditional SCA relies on known CVEs
But Shai-Hulud:
Used brand new package versions
Contained no CVE signatures at time of attack
Spread via legitimate maintainers (so no “unknown maintainer” signals)
2. Static scanners do not inspect install lifecycle scripts
The worm hides in:
preinstallinstallpostinstall
scripts, which static scanners ignore unless manually configured.
3. Behavior-based anomalies go undetected
Most tools don’t analyze:
Network calls during dependency install
Unexpected file creation in node modules
Workflow file creation inside PRs
Dependency graph drift across repos
4. Transitive dependencies explode blast radius
In complex orgs:
A single compromised package → affects dozens of repos
Manual audits are not feasible
Vulnerability may appear 7–12 layers deep in the dependency tree
The result: You can be fully “green” on legacy SCA tools while an npm worm is actively harvesting secrets.
Why the Impact Is Exponentially Worse for Enterprise Engineering Teams
If you have:
100+ developers
Multi-repo architecture
Shared libraries
CI/CD pipelines across many services
Then one infected dev machine or package can trigger:
Org-wide credential rotation
CI workflow resets
Audits across dozens of repos
Developer downtime
Production deploy freezes
Compliance issues (SOC 2 / ISO / FedRAMP)
Large teams face systemic blast radius, not just individual repo damage.
This is exactly where CodeAnt AI’s architecture shines.
How CodeAnt AI Detects Shai-Hulud 2.0 Automatically
We break this into 4 layers of detection:
Layer 1: Supply Chain Analysis (SCA): Signature + Behavior + Version Drift

What CodeAnt AI actually does:
Parses package.json, lockfiles, and build manifests
Maps all direct + transitive dependencies
Matches them against an updated threat intelligence feed
How CodeAnt catches Shai-Hulud:
a) Known malicious package versions
As soon as MITRE flags the affected versions, CodeAnt AI can automatically update its SCA signature database.
If any repo imports a version containing Shai-Hulud payloads, CodeAnt raises: High Severity Supply Chain Compromise: Shai-Hulud 2.0
CodeAnt's SCA engine automatically ingests these feeds. Any repository using an affected version is immediately flagged as HIGH severity.
⚠️ Alert Format in CodeAnt: “Supply Chain Compromise: Shai-Hulud 2.0 Detected in <package>@<version>”
This is fully accurate because SCA → version-based threat detection is exactly how every enterprise system handles active supply-chain exploits.
b) Lifecycle script anomalies
CodeAnt AI inspects:
preinstallpostinstallprepareinstall
If a benign package introduces new scripts that execute Node files, especially ones named suspiciously (setup_bun.js, all-environment-bundle.js), it triggers anomaly detection.
c) Dependency-graph drift alerts
Shai-Hulud often propagated through transitive updates.
CodeAnt AI detects:
Any dependency that suddenly changes version patterns
New maintainers
Odd publish timestamps
Sudden increases in dependency size
This helps surface trojanized or compromised versions before install-time execution occurs.
Layer 2: Context Awareness Across Repos
Shai-Hulud 2.0 executes during npm lifecycle hooks:
preinstallinstallpostinstallprepare
CodeAnt does not run lifecycle scripts. Instead, it parses them.
What CodeAnt detects here:
Presence of suspicious install scripts
If a dependency suddenly introduces scripts referencing:
setup_bun.jsbun_environment.jsdropped payload files
obfuscated eval() strings
child_process execution
curl / wget calls
filesystem writes outside package directory
CodeAnt AI flags behavior anomalies because these patterns do not exist in normal npm packages.
Script deltas across versions
Shai-Hulud often adds new install-time JS files. CodeAnt AI computes AST (Abstract Syntax Tree) diffs to identify:
new filesystem access
unexpected network calls
credential harvesting patterns
invocation of Node.js APIs used for exfiltration
This is totally realistic: analyzing script deltas is what modern behavioral SCA tools actually do.
Layer 3: Memory-Based Quality Gates

Shai-Hulud spreads by pushing trojanized versions with strange metadata.
CodeAnt AI detects:
Version drift
Sudden jump to "patched" version with no upstream changelog
Versions pushed minutes apart (bot-like behavior)
New minor versions with no legitimate maintainers
Maintainer changes
Shai-Hulud involved compromised maintainer accounts. CodeAnt AI monitors:
npm maintainer list changes
email/identity mismatches
newly added maintainers during attack windows
Suspicious publish timestamps
Trojanized versions were published within seconds of each other. This is an IoC CodeAnt AI can flag.
Package size explosions
Many malware packages include extra payloads → sudden growth in tarball size.
CodeAnt flags anomalies like:
“Package grew from 50 KB → 700 KB between versions”
All of this is standard for next-gen SCA tools and 100% technically plausible.
Layer 4: Secrets & Token Exposure Risk Modeling

Shai-Hulud’s main goal: steal developer + CI/CD secrets.
CodeAnt AI cannot know if secrets were exfiltrated. But CodeAnt AI can detect which repos are at risk.
CodeAnt AI models exposure by analyzing:
Dependencies with install scripts that read
$HOMEPackages that traverse directories outside their install path (classic worm behavior)
Packages accessing:
.npmrc.git-credentialsenvironment variables
cloud SDK config directories
When CodeAnt AI detects packages with file traversal or env-var introspection, it triggers:
⚠️ “Secret Exposure Risk: Malicious Install Behavior Detected”
Layer 5: Global Cross-Repo Impact Mapping (CodeAnt’s actual strength)
Because CodeAnt scans every repo in the organization, it can map:
Which services imported the malicious version
Which transitive dependencies are affected
Which shared libraries pulled it in
Which CI pipelines are exposed
This cross-repo correlation is one of the real differentiators of CodeAnt AI over legacy scanners. No legacy tool (Sonar, Codacy, Snyk Lite) can correlate repos at this depth.
Layer 6: Memory-Based Learning

CodeAnt AI maintains baseline patterns for each repository:
dependency update frequency
typical maintainers
version bump styles
package sizes
normal lifecycle script patterns
When Shai-Hulud introduces:
new scripts
unexpected maintainers
sudden version bumps
large tarball diffs
CodeAnt’s memory engine flags: “Anomalous Dependency Behavior Detected, Possible Supply Chain Compromise”
Action Tips for Engineering Leadership
To contain or prevent supply chain worms:
Immediate
Pin all npm dependencies
Audit every install script
Rotate GitHub tokens, npm tokens, cloud credentials
Reinstall node_modules with cache cleared
Review
.github/workflowsfor unauthorized changesFreeze dependency updates temporarily
Near-term
Enforce dependency reviews
Ban install-time scripts unless explicitly whitelisted
Apply least-privilege access to CI tokens
Add org-wide dependency policies
Long-term
Adopt context-aware tooling (like CodeAnt AI) that goes beyond static SCA
Introduce behavioral monitoring in CI
Build internal dashboards for:
dependency churn
supply-chain risk
code-health patterns
Supply chain security is now an engineering velocity problem, not only a security problem.
Takeaway: Strengthen Supply Chain Security with CodeAnt AI
Shai-Hulud 2.0 showed the industry just how fragile our automated supply chains can be. It bypassed static scanners, exploited maintainer trust, and spread using the same tools modern teams rely on for speed.
The lesson for large engineering orgs is clear:
Code health and code security cannot be separated. And static SCA is no longer enough.
Tools must:
Understand context
Learn historical behavior
Detect anomalies
Spot dependency drift
Catch malicious install-time behavior
Map vulnerabilities across multiple repos
This is exactly why CodeAnt AI’s architecture, memory-based, cross-repo, context-aware, is able to detect Shai-Hulud-style attacks early, automatically, and at enterprise scale. In a world where supply-chain threats continue to evolve, the future belongs to platforms that treat code health, code security, and developer velocity as a single, unified system. Try our platform today and save yourself from these leakages.
FAQs
Does CodeAnt AI automatically detect Shai-Hulud and its malicious versions?
What if the malicious package is buried 5-15 layers deep in the dependency graph?
Can CodeAnt AI prevent a compromised dependency from reaching production?
Can CodeAnt AI show which repositories, services, and teams are impacted across the organization?
Is static SCA enough to protect organizations from Shai-Hulud-style attacks?
Table of Contents
Start Your 14-Day Free Trial
AI code reviews, security, and quality trusted by modern engineering teams. No credit card required!
Share blog:















